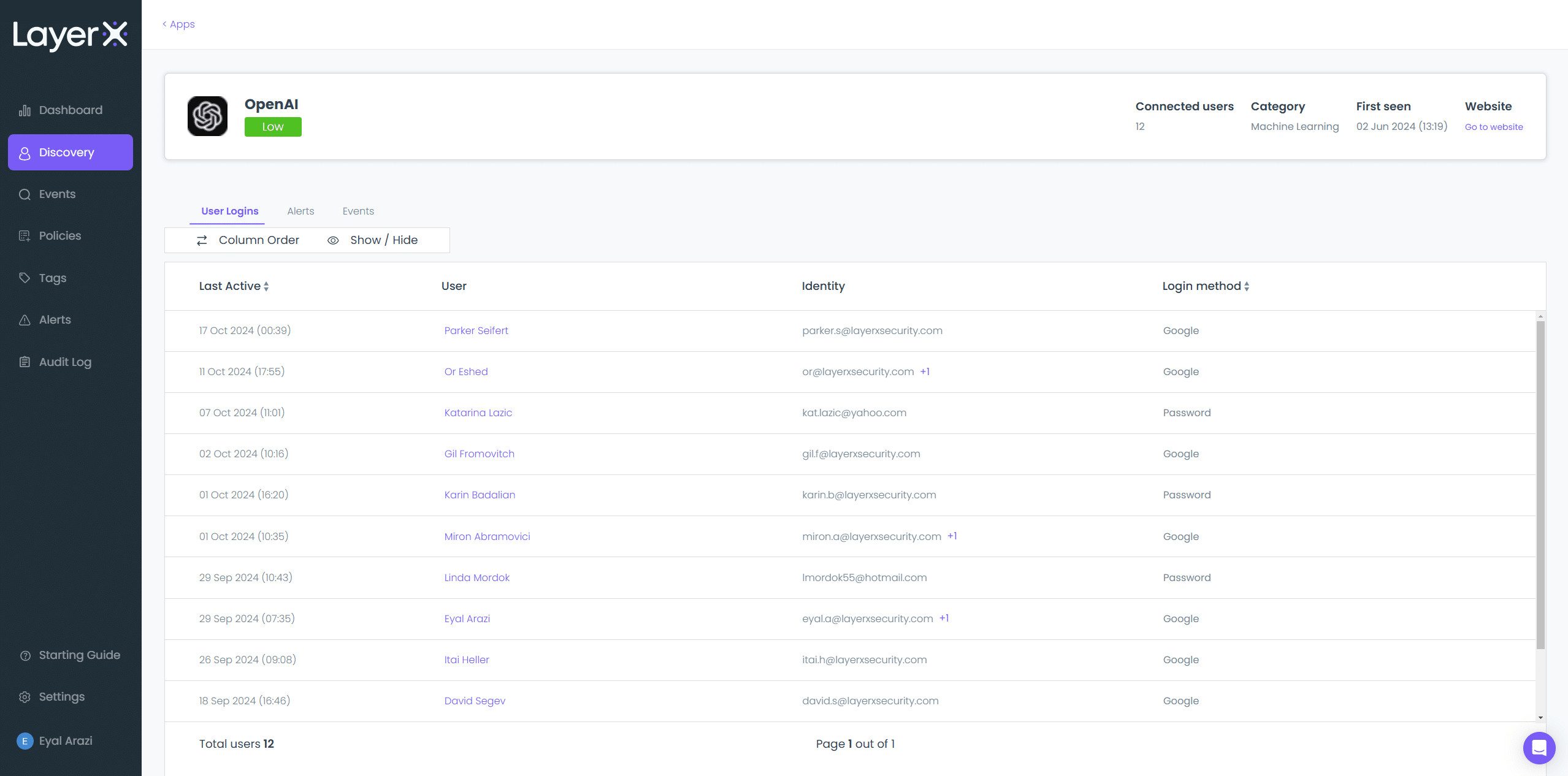
GenAI Security
The Challenge
GenAI tools enable a significant productivity boost, but also expose organizations to data leakage by sharing sensitive corporate data with LLMs.
The Solution
LayerX allows organizations to map GenAI usage in the organization, enforce security governance, and restrict sharing sensitive information.

Web/SaaS DLP & Insider Threat Protection
The Challenge
The ease of use and availability of file-sharing SaaS apps and online shared drives make it the #1 channel for inadvertent or malicious data leakage.
The Solution
LayerX allows organizations to track all file-sharing SaaS apps and online drives and to control user activity in them, to prevent accidental or malicious data leakage.

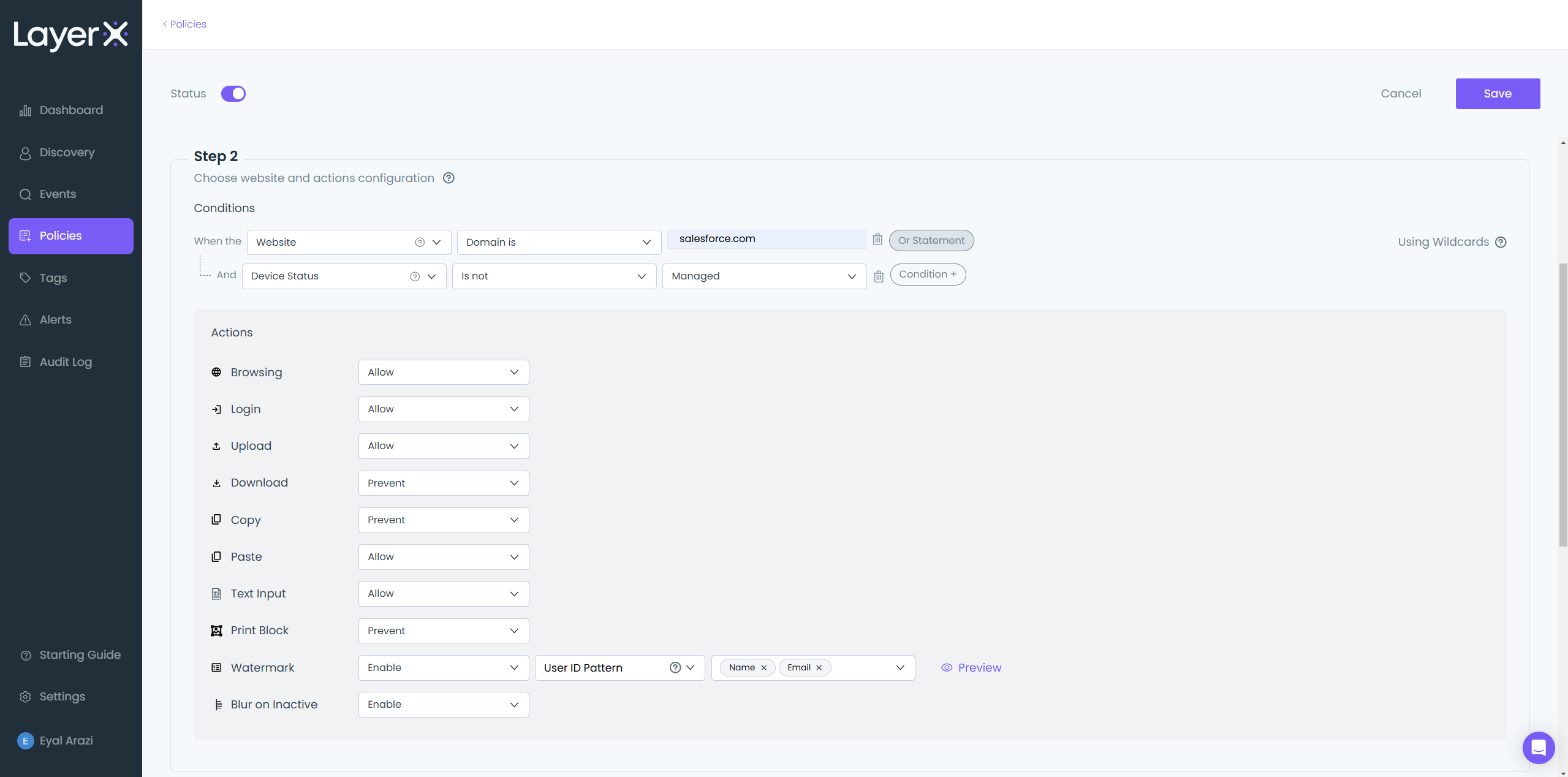
Shadow SaaS & SaaS Security
The Challenge
Most enterprise applications today are SaaS-based, but organizations lack tools to properly secure SaaS usage or identify unsanctioned ‘shadow’ SaaS apps.
The Solution
LayerX provides full audit of all SaaS applications and users in the organization, and applies granular, risk-based guardrails over all SaaS usage.