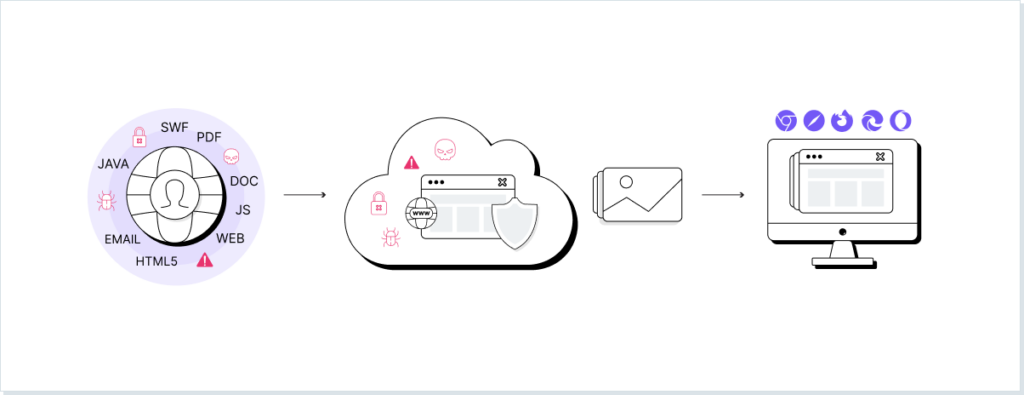
One of the most overlooked threats to company security is something employees spend 40% of their waking hours doing. With organizations enjoying the benefits of an increasingly hybrid workforce, too many have made this key oversight in how users and employees interact with external systems. Browsing the web comes with considerable, often-ignored risk.
When visiting a web page or app, your device’s browser loads code from a remote server. From a zero-trust perspective, the assumption of this server’s legitimacy raises serious concerns. Traditional browser protection such as Secure Web Gateways (SWGs) focused on attempting to verify a webpage via a pre-built list of suspicious links; this contextless approach hindered genuine requests and often completely missed new attacks.
A decade ago, techniques such as remote browser isolation have been introduced as the next generation of browser protection. What remote browser isolation does is load and verify site code before it reaches the browser. Offering more contextual protection, this approach physically isolates a device from hard-coded threats.
Below, we take a closer look at the threats that browser isolation protects against, and why organizations use it. We ask if it offers adequate protection in an evolving threat landscape that demands seamless, organization-wide security and review more modern and effective security technologies to face browsing risks.
Which Threats Does Browser Isolation Protect Against?
Browser isolation protects against opportunistic security events. Below are the 6 major vulnerabilities faced by unprotected end-users:
- Malvertising. This attack centers around legitimate advert networks. To the genuine site operators – and their third-party ad manager – these ads look entirely normal. However, the criminal operators of these ads have included a few lines of malicious code. When an unprotected browser loads an infected page – which can be any ad on any site – a single instruction is loaded onto your device, connecting it to the criminal’s command and control server. From here, the C2 server can swiftly and quietly download anything in the background.
- Drive-by downloads. This broad category of attack describes a stealthy malware installation process. Whether you’re simply loading a webpage with an unpatched browser vulnerability, or installing a genuine piece of software with malware bundled into the loader, drive-by downloads take advantage of any small oversight.
- Redirect attacks. When an email promoting major discounts at a brand bounces into someone’s inbox, a security-minded user will hover over the link to check its validity. Seeing the URL beginning with the brand’s own site address, they assume all is fine. However, redirect URLs allow for the attacker’s site to be smuggled into an address that first appears legitimate. This technique was found in nearly 7,000 phishing emails masquerading as American Express and Snapchat in the 3 months between May and July 2022.
- Click-jacking. The classic vulnerability that allows a user to be fooled into clicking any unintended link. Fake ‘download’ and close ad’ buttons abound, tricking users into generating fake ad revenue and even initiating a malware download.
- On-path browser attacks. Sitting between the site server and your own browser, an on-path attacker can steal your cookies or exploit the HTTP connection to collect login credentials, and even alter the web content you’re viewing.
- Cross-site scripting: This sees an attacker inject code into a legitimate website; the payload for which is dropped when the victim loads the website. Similar in style to the redirection attack, some cross-site scripting adds malicious code onto the end of a trusted URL. When the victim’s web browser loads this, an attacker is able to steal login credentials and more.
How Does Browser Isolation Work?
Browser isolation technology distances webpages from the user’s own browser. This can take a number of different forms (see the types of browser isolation below), but all work off the same general premise. First, a web user’s browsing activities are conducted in an isolated setting. This can be a server, controlled and maintained by a cloud vendor, or a sandbox within the end-user’s own computer. From there, the browsing behavior is transmitted back to the user’s device, as are their requested web pages (or simulations thereof). When the user submits a form, requests a download, or clicks on a link, the request is first transmitted to this isolated container, where it’s carried out and assessed for malware.
For instance, a user has surfed across an innocent-looking site, holding information on an upcoming industry event. Unknown to them, however, a malvertisement campaign is targeting this exact page. While an unprotected user risks an automated malware download, the isolated container protects the user from any attempt to send them to an unrecognized command and control server, completely disabling the attack. This server or sandbox operates on a non-persistent basis, being reset or deleted whenever the user closes the session, or the browser times out. This nullifies the risk of cross-site scripting and other JavaScript-based attacks, removing them from the individual employee’s concerns, and helping seal web browsers off from the company’s broader attack surface.
Why Do Organizations Use Browser Isolation?
Gartner’s recent survey found that 82% of industry-leading respondents throughout the finance, HR, and legal industries will continue to support remote working. With traditional perimeter security now scattered throughout hundreds of different premises, spiraling data breach costs are proving the necessity for better remote protection.
The traditional option for protecting against web-based malware has included tools such as the secure web gateway (SWG). This network security solution acts as a proxy between the end-user and the page they’re trying to connect to. Unfortunately, SWGs fail to dynamically identify – and therefore protect from – malicious pages in real time. Many web proxies and similar tools suffer from browsing session context blindness, while missing the fine details between genuine web destinations and malicious instances. The wide range of approaches employed has seen web browser solutions begin to suffer from tech stack bloat. Furthermore, these complex approaches can still miss zero-day exploits, while unnecessarily blocking users from sites and thereby crashing productivity.
Web browser isolation distances internal networks from any threat. This facilitates both the productivity of employees – and their safety.
Types of Browser Isolation
There are three broad categories of browser isolation techniques.
#1. Remote browser isolation
Remote browser isolation relies on the end-user’s browsing behavior being streamed to an isolated cloud server. There are three different forms of remote isolation, each sending content to the user’s device in different forms. The first is the ‘pixel pushing’ method. This sees a cloud server load the webpage code, while streaming a video or sequential images of the user’s browsing activities to the end-user’s device.
DOM rewriting, on the other hand, sees the server load the webpage, and then actively rewrite it in order to remove any malicious HTML or JavaScript. Once the content is declawed, it’s sent to the end-user’s device to be loaded a second time by the browser and displayed.
The final method involves a similar process, wherein the webpage is loaded remotely, but the content is not extensively rewritten. Instead, the user receives a representation of the web page in vector graphic format after all code has been executed.
Fundamentally, remote browser isolation almost always introduces latency into the browsing process.
#2. On-premises browser isolation
On-premises browser isolation works in a similar manner to remote browser isolation. However, in order to cut down on latency, the remote cloud server is replaced with a server hosted within the organization’s internal network.
The web browser isolation must almost always occur within the organization’s existing firewall procedures, instead of outside it, as occurs via the remote isolation process. This technique can work well for the highest-privacy organizations, though does not apply as nicely to remote workforces thanks to the costly hardware demands of on-premises servers. Furthermore, while users are safe in the knowledge that their browsing will not expose individual devices, there is the risk that the internal network is hit with a particularly nasty threat from the public internet.
#3. Client-side browser isolation
Client-side browser isolation is drastically different from remote browser isolation. Operating under the same browser virtualization ethos, it doesn’t rely on an external server but instead operates on the user’s device itself. The isolation aspect comes from one of two techniques: virtualization, or sandboxing.
Virtualization describes the process of dividing one computer into multiple – separate – virtual machines. Just below the operating system of a computer sits the hypervisor, which can be used to split the hardware’s resources between the host device and any guest systems. What happens in one virtual machine should – theoretically – be isolated to just that. By using one virtual machine to load web pages, the host computer is kept safe from the most common web browser threats.
Sandboxing holds a few similarities to virtualization, offering a contained virtual environment within which applications can be run. However, there is no creation of a wholly separate system. Instead, a sandbox is a container that can be placed around an application running on the operating system. The key benefit of this is that – every time a sandbox is closed – all events remain unsaved, and hence discarded.
The next generation of browser security starts with LayerX
Browser isolation is not delivering on the sweeping security it once promised. The solution’s significant impact on user experience has resulted in sporadic usage, with organizations attempting to rely on patchy protection as employees simply choose a less burdensome browser experience.
Alternatives aren’t much better, either: Cloud Access Security Brokers (CASBs) have long been the industry’s solution to browser vulnerability. However, the policy adherence enforced by CASBs only apply to sanctioned applications, and are deeply dependent on the API of each app. Their integration requirements have helped create a complex, costly, and less efficient form of security management.
LayerX is the first solution to prioritize simplicity. It uniformly delivers every strength of remote browser isolation, allowing real-time governance of web usage, phishing, and malware protection, while not getting in your employees’ way. Throw out large-scale infrastructural changes, LayerX’s solution works to wrap to your organization’s security needs – not the other way around.