One of the oldest and most established cybersecurity architectures today is the air-gap model. First established during World War II, the sounds produced by early electromechanical encryption devices could be recorded and descrambled to reveal military communications. Commanders were advised to control physical access to both the electromechanical devices and the surrounding 30 meters – thus, the air-gap model was born.
Security via physical isolation has remained a powerful component to today’s NATO certification standards. Recent strides toward cloud-based infrastructure may have shattered the traditional perimeter, but air-gap security has evolved in response. For instance, innovation has never before been more heavily dependent on constant internet connection. Browsing sites requires the transfer of data to and from untrusted servers, making the browser one of today’s most vital enterprise tools – and largest security oversight.
Browsing the public-facing internet is so ubiquitous that it often slips under the security radar, but cybercriminals have already released the limitless potential of browser-borne malicious code. 2023 has begun with a massive spike in malvertising cases, with consumers and businesses alike falling foul to trojanized download pages and malware-infested Google Ads.
Remote Browser Isolation (RBI) offers one method of protection by abstracting browsing away from the trusted device. Achieved via virtualization technology, RBI physically separates a trusted device from a website’s unknown server. A single isolated environment – such as a remote cloud instance – actions the user’s browsing behaviors, while streaming the resulting pages and actions to the end-user’s own browser. Any malicious code hosted on the website is therefore kept at arm’s length, while the user is still free to browse sites at will.
Offering almost unbeatable protection has made RBI one of today’s most popular forms of browsing defenses. However, the enterprise-wide protection offered by RBI is only as good as its slowest internet connection; while some organizations continue to battle RBI’s persistent bandwidth issue, others have discovered a solution that no longer pits productivity against security.
Learn about the LayerX browser protection platform
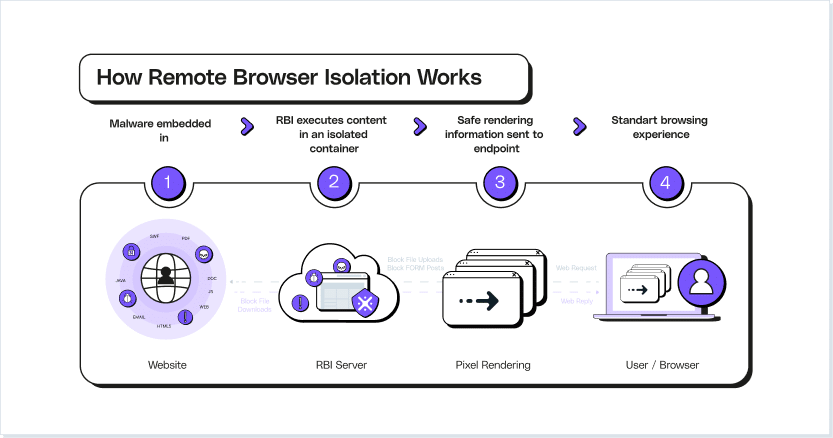
How Does Remote Browser Isolation Work?
Remote Browser Isolation can take a number of different forms, but all broadly operate off the same mechanisms. Firstly, an authenticated user requests a newly isolated browser instance. The solution assesses which permissions that user has access to (already defined by enterprise-wide zero-trust policies), and creates the browsing instance accordingly.
The isolated browser can be hosted via three different isolation architectures. The first and most popular is as a container, on a third-party cloud instance, though other options include on a virtual machine, or as a sandbox. These latter two can be hosted within the user’s own device, depending on the solution.
With this isolated instance set up, end-users interact a little differently to the world wide web. Websites are simply lines of code, hosted on a web server. When browsing on an unprotected device, the browser app reaches out to this server and downloads all necessary content to run each page. While perfectly fine for legitimate pages, there are a number of ways this process can be abused to silently download malware in the background. Once an RBI process is up and running, all code is executed on the separate instance. From there, the browsing behavior of the end-user is streamed to their own device, facilitating almost real-time feedback.
This separate virtual browser will have its own threat detection capabilities, monitoring site code for recognizable threats. This sanitization of session data and URLs allows end-users to still interact with and browse any site – there’s lower risk of users being blocked out of sites they may genuinely need access to. Not only does a suitable RBI solution prioritize web security, it also helps reduce the impact of blocked sites on user productivity, cutting attackers out of the equation.
Types of Remote Browser Isolation
The types of Remote Browser Isolation each provide their own situation-specific advantages. The security stance of every organization needs to be reflected in the tools protecting employees and customers. Varying from uber-secure to lighter, more user-friendly experiences, here are the three major types of RBI:
Pixel Pushing
This RBI technique sees the cloud vendor remotely load and execute every webpage, replicating the user’s browsing behavior via pixel images. This stream is then transmitted to the client’s browser, demanding no change from the user’s preexisting browsing habits. Furthermore, this approach can work across almost all webpages. This form of cloud browser isolation offers almost unbeatable security, as files and executable code never have to interact with the end-user’s device.
However, this high degree of security is only applicable while the solution is in use. A major disadvantage of pixel pushing is the latency introduced to almost all browsing behavior. This poor user experience can lead to instances of end-users outright refusing to use the security solution built to protect them.
DOM-based rendering
Whereas pixel pushing streams content to the viewer, DOM rewriting takes a more active approach to combating malicious code. This method first loads the website in question in the isolated environment, before rewriting all content within. This removes any potential attack from the source code itself, and only after the extensive rewriting is the web content sent on to the end-user. Finally, the browser loads and executes the declawed site.
Streaming media
Once a web page fully loads and all code is executed by the cloud vendor, a vector graphics representation of the webpage is created. This render of the page allows for low-risk media to be quickly provided to the browser. Though often faster than pixel pushing, there are still weaknesses to this solution, such as a far higher bandwidth consumption than unprotected browsing takes up. This has knock-on effects to computational costs, as encrypted video and vector graphics demand more resources to reach the end-user.
Benefits of Remote Browser Isolation
Malicious websites represent one of the most glaring security flaws in any organization. Websites can sit in a variety of hotspots throughout the attack funnel – from malware-loaded advertisements that deploy on legitimate sites, to payload-delivering fake sites linked from phishing emails. RBI protection needs to comprehensively address every potential attack avenue for every user in your organization.
Protection From Malicious Code
RBI prevents malicious code from hitting any part of the vast, sprawling network of enterprise devices. By focusing on a zero-trust approach, malicious code protection is no longer dependent on traditional file signature-based detection techniques, growing to encompass even novel malvertisement and phishing attacks.
Anonymous Browsing
Today’s increasingly interconnected workspaces see employees regularly bringing in and working from devices they’re most comfortable with – including their own personal phones and laptops. The browsing caches of each device contains loads of personal information, with auto-fill representing the largest menace to data security. By offering a form of connection that offers every device on the network anonymous browsing, attackers can no longer attempt to steal auto-fill and data-full end-user profiles.
Data Loss Prevention
Each browser cache offers a wealth of data that can be leaked reasonably easily. By removing local caching, the end point device is removed from the attacker’s scope. On an enterprise-wide level, the higher visibility granted to each website’s code allows for the identification and termination of any attempted data exfiltration.
User Behavior Analytics
A safe browser isn’t the only benefit boasted by RBI. Most RBI solutions offer a central dashboard that displays an overview of each organization’s web security. Not only does this offer a macro view of your security stance, but further supports the management of granular data at a user level. Reports of web usage and browser activity allow for individual users to be better guided to safer browsing habits.
Reduced Number of Security Alerts
By running all active code outside the network itself, no threat is able to penetrate to the network layer. This takes the burden off detection-based solutions, the security alerts of which makeup the vast majority of most security teams’ backlog. The zero-trust approach that forms the foundation of RBI allows security teams the freedom to focus on improving the wider security stance of the surrounding enterprise.
Challenges of RBI
Despite the numerous security advantages offered by RBI, the tighter security is only applicable if the solution’s challenges prove surmountable. The following challenges range from issues surrounding the user experience, to incomplete protection:
Latency
The process of diverting all of the user’s browsing traffic via a cloud-based container takes a lot more time for this data to reach its intended target. By essentially doubling the number of stops being made by each packet, latency is a major concern voiced by end-users. This issue doesn’t just degrade the UX, but further harms productivity and can even result in users choosing to forgo any protection.
Website Support
There’s no guarantee that every website is able to withstand the transformative processes taken by RBI. Pixel pushing demands the page to be run in a remote browser – which may not be able to render all page elements. Furthermore, DOM-based rendering is an even more intensive process and complex web pages may be broken entirely when content is stripped from them.
Incomplete Protection
The protection offered by DOM rendering still requires external code to be run on the end-user’s own browser. The foundational goal of DOM is to rewrite this, though there are attack vectors that can work their way around even advanced threat detection. For instance, an advanced phishing page can conceal malicious content as other forms of web page elements. This would then allow malware past the web browser isolation.
Expense
Rerouting and analyzing the entirety of an organization’s web traffic is no small demand. The extra expenses of these cloud solutions can lead to enterprises making difficult budgetary sacrifices for a solution that may not offer complete security.
Protect Your Browsing with LayerX
Remote browser isolation suffers from some key reliability and budget challenges, largely as a result of its outdated, network-only approach to browser protection. LayerX provides an opportunity to regain the potential of web browsing, while maintaining the highest level of enterprise security via a single browser security platform.
LayerX revolutionizes browser protection in two key ways – detection and enforcement. Firstly, the process of high-precision threat detection is focused around each end-user’s browsing activity. The proximity to each end-user allows direct visibility into all browsing events post-decryption, offering a true deep-dive into your enterprise’s security stance. This is enabled via a lightweight browser extension that benefits from full granular visibility into each site component, request, and file. While each user’s website activity is scouted in order to establish malicious intent, the extension’s sensor components feed all of this browsing data into an independent analysis engine. This ML algorithm provides real-time threat detection, bulked out by LayerX’s own always-on threat intel.
If all code is found to be legitimate, the browser is free to load such code with no interruption. If, however, a page element is discovered to be hiding malicious intent, LayerX’s high-precision enforcement process kicks in. Any component within the accessed web page can be modified in real-time, preventing the code’s interaction with the end-user’s browser and therefore the theft or exfiltration of data, cookies, and credentials. This process goes far beyond the crude block/allow processes of many browser protection solutions, and avoids the latency-intensive demands of complete DOM-based rendering.
Even while providing the highest form of browsing security, LayerX goes further. LayerX’s dedication to zero trust enables the browser itself to become another form of authentication throughout the enterprise. This helps lock down organizational resources even across contractor-heavy spaces. Once the browser is viewed as a further form of authentication, it becomes possible to enforce authorization policies at the browser level, helping mitigate excessive privileges across both managed and unmanaged devices.
Finally, LayerX’s granular insights are condensed into the management console. Adapt and change policies across the entire enterprise – or specific subsections – based on next-generation threat intel and oversight.