A new phishing attack campaign, targeting Mac users and identified by LayerX Labs, shows the trials and tribulations of combating online phishing, and how attacks morph and shift in response to adaptations by security tools.
For the past few months, LayerX has been monitoring a sophisticated phishing campaign that initially targeted Windows users by masquerading as Microsoft security alerts. The campaign’s goal was to steal user credentials by employing deceptive tactics that made victims believe their computers were compromised.
Now, with new security features rolled out by Microsoft, Chrome, and Firefox, the attackers have shifted their focus to Mac users.
Act I: Targeting Windows Users
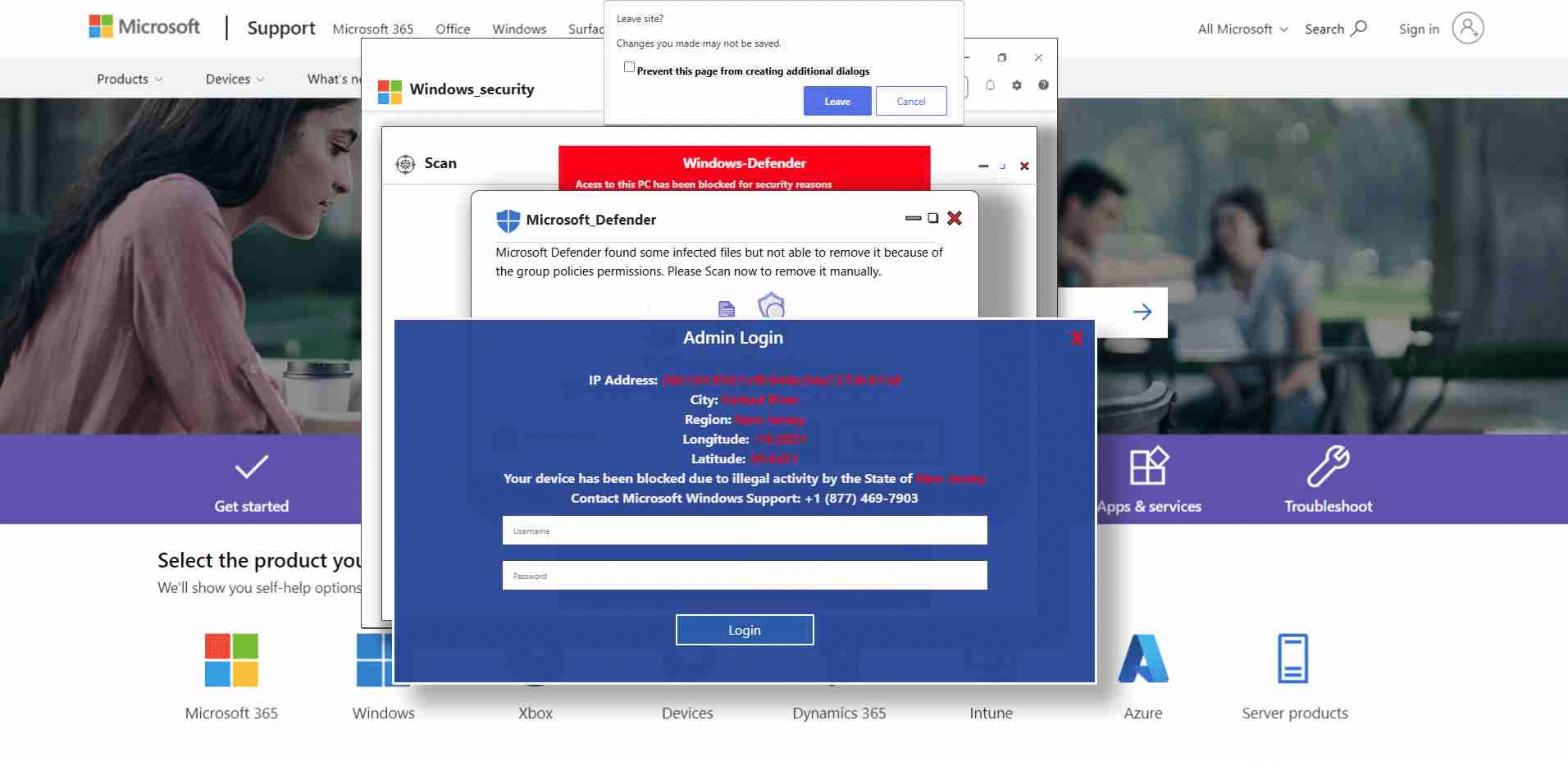
The original phishing attack involved compromised websites displaying fake security warnings claiming that the user’s computer had been ‘compromised’ and ‘locked.’ The attackers prompted users to enter their Windows username and password. Simultaneously, malicious code caused the webpage to freeze, creating the illusion that the entire computer was locked.The original phishing attack involved compromised websites displaying fake security warnings claiming that the user’s computer had been ‘compromised’ and ‘locked.’ The attackers prompted users to enter their Windows username and password. Simultaneously, malicious code caused the webpage to freeze, creating the illusion that the entire computer was locked.
LayerX has previously written about this campaign on our blog.
Why This Campaign Was Difficult to Stop:
- Hosted on a Microsoft Platform – The phishing pages were hosted on Microsoft’s Windows.net platform (an open platform by Microsoft for hosting Azure applications). In the context of the attack, this made the messages appear legitimate, since they were security warnings (supposedly) by Microsoft, coming from a page on a windows[.]net domain.
- Exploiting Hosting Services – Another common tactic that was used by attackers in this case was to use a trusted hosting service as the underlying infrastructure for malicious pages. The reason for this is that traditional anti-phishing defenses such as Secure Web Gateways (SWGs) and email security solutions often assess page risk based on the domain’s reputation of the Top Level Domain (TLD). In this case, the TLD (windows[.]net) is a well-known and highly-used platform by a reputable provider (Microsoft), with a high TLD reputation score. As a result, these pages were able to circumvent traditional protection mechanisms.
- Randomized, Quickly-Changing Sub-Domains – under the general top-level domain of windows[.]net, attackers served their malicious code from randomized, rapidly-morphing subdomains. This meant that even if a particular page was flagged for being malicious and placed in feeds of malicious pages, it was quickly taken down and replaced by another URL with a ‘clean’ reputation. Because of the highly random subdomain URLs, attackers could do this over and over, while still maintaining the attack.
- Highly Sophisticated Design – Unlike typical phishing pages, these were well-designed, professional, and frequently updated to avoid detection by security tools relying on known phishing signatures.
- Anti-bot and CAPTCHA technologies – in some variations, LayerX observed that the page code included anti-bot and CAPTCHA verification. This was done to blog automated web crawlers of anti-phishing protections and delay the page’s classification as malicious.
The result was a sophisticated, highly effective, and long-running campaign. LayerX has been following this campaign for over a year. However, in late 2024 and early 2025, we observed an increase in the intensity and volume of this campaign, which was a testament to its effectiveness.
This was noticed by Microsoft, as well, who in February 2025 introduced a new ‘anti-scareware’ feature in the Edge browser to combat these attacks. Around the same time, similar protections were implemented in Chrome and Firefox.
Act II: New Protections Render the Old Campaign Useless
Following the introduction of these browser protections, LayerX observed a drastic 90% drop in Windows-targeted attacks.
LayerX was still observing some similar malicious pages, meaning that the campaign infrastructure was still online. However, users were not reaching it.
We attribute this drop in the new ‘anti-scareware’ features by Microsoft (and others), that were blocking these attacks.
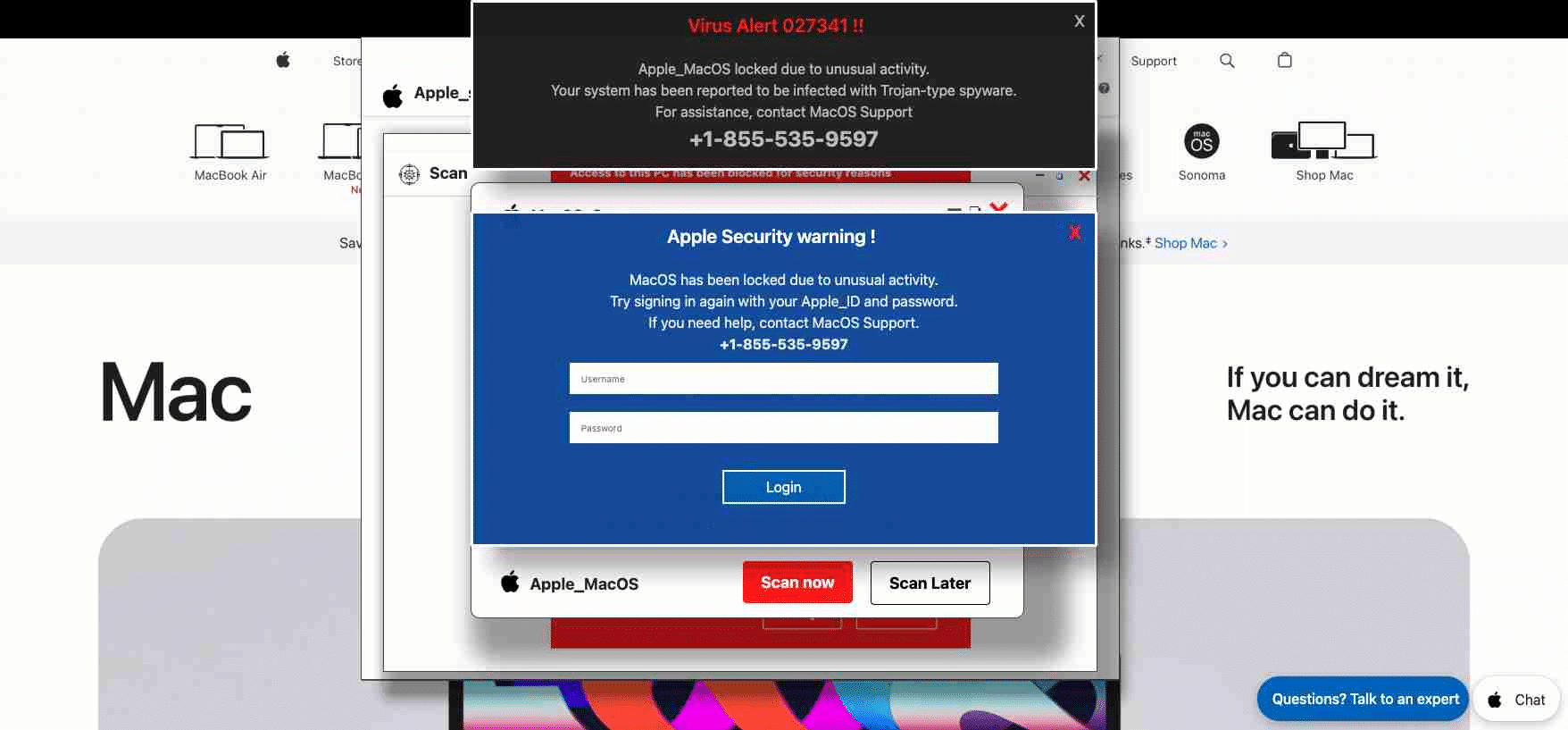
Act III: The Campaign Morphs to Target Mac Users
However, it seems that LayerX was not the only one to observe a drop in the success rate of attacks – the hackers behind it noticed it, too.
Their response: modify the campagin to target a group of unprotected users – in this case: Mac users.
Within 2 weeks of Microsoft rolling out the new anti-phishing defenses, LayerX begun observing attacks against Mac users, who – apparently – were not covered by these new defenses.
Before this, LayerX has not observed attacks on Mac, but only against Windows users.
The new phishing attempts were visually nearly identical to the attacks targeting Windows useres, except for a few critical modifications:
- Phishing page layout and messaging redesigned to appear legitimate to Mac users.
- Code adjustments to specifically target macOS and Safari users by leveraging HTTP OS and user agent parameters.
- Continued use of Windows[.]net infrastructure, maintaining the illusion of legitimacy.
How Victims Were Lured In
LayerX’s investigation revealed that victims were redirected to the phishing pages via compromised domain ‘parking’ pages:
- The victim attempted to access a legitimate website.
- A typo in the URL led them to a compromised domain parking page.
- The page quickly redirected them through multiple sites before landing on the phishing attack page.
In one specific case, the victim was a macOS and Safari user working for a LayerX enterprise customer. Despite the organization employing a Secure Web Gateway (SWG), the attack bypassed it. However, LayerX’s AI-based detection system, which analyzes web pages using over 250 parameters at the browser level, identified and blocked the malicious page before any damage was done.
Act IV: The Battle Goes On
The new Mac-targeted attacks required relatively minimal modifications by hackers of their existing infrastructure – primarily text changes and some code changes to target MacOS and Safari users.
This attack campaign underscores two critical points:
- Mac and Safari users are now prime targets – While phishing campaigns targeting Mac users have existed before, they have rarely reached this level of sophistication.
- Cybercriminals are highly adaptable – As security measures evolve, attackers continue to modify their tactics, proving that organizations need advanced, proactive security solutions.
Based on the longevity, complexity, and sophistication displayed by the actors behind this attack campaign thus far, we suspect that this is just a first response by them, as they adapt their attacks to new defenses.
Our prediction is that in the coming weeks or months, we will see a resurgent wave of attacks based on this infrastructure as it probes and tests for weak spots in Microsoft’s new defenses.
This is just the latest reminder that preventing phishing and web attacks is a continuous, never-ending battle.
Until the next chapter…