LayerX Labs identified a new zero-day phishing campaign that impersonates Microsoft security notifications to lure victims into sharing their login credentials and payment details.
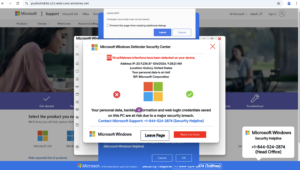
The attack mimics a Microsoft Windows Defender security alert, urging users to call a hotline number, enter their credentials, and provide payment to the call center to ‘secure’ their computer.
This attack was able to penetrate traditional network security mechanisms such as Secure Web Gateways (SWGs) and Security Service Edge (SSE) solutions because it uses a number of evasion techniques designed especially to evade traditional security tools
In this blog, we’ll share the details of this incident, explain what makes it unique, explain why it slipped through traditional security mechanisms, and how you can protect yourself (and your organization) against similar attempts.
The Incident: A Microsoft Alert Scam
This attack was identified in the environment of one of LayerX’s large enterprise customers, where it bypassed several layers of network security controls, but was automatically blocked by LayerX before it could cause harm.
The attack employs a simple yet effective strategy—a webpage resembling a Microsoft Windows Defender alert claiming their computer has been infected with malware.
The message claims that the user’s device was infected with malware, urging them to call a support number for immediate assistance.
Users who attempted to leave the page were shown a message claiming their device was locked, which required them to enter their credentials to log in.
In some cases we’ve tested, the page code was able to cause the web browser to freeze, mimicking a security block by Microsoft and again prompting them to call the fake security helpline number.
This type of social engineering preys on the urgency and anxiety of unsuspecting users. By simulating a security emergency, attackers prompt users to act immediately so they don’t take the time to scrutinize the alert too closely.
Multiple Layers of Risk
Attackers commonly use phishing tactics to trick users into sharing information or providing access to systems. Without advanced detection in place, users could have been exposed to the attack, putting them at risk of:
- Calling the provided hotline number, where attackers could manipulate them into paying a ransom or granting remote access to their systems.
- Entering their credentials to the phishing site, which the attackers could steal and use for account takeovers.
- Their user information being leveraged for more sophisticated attacks or being sold on the dark web.
Why Conventional Defenses Failed
Many organizations deploy Secure Web Gateway (SWG) solution to deal with browsing threats and phishing attacks. Nonetheless, this attack was detected at a LayerX customer, where this attack bypassed the organization’s SWG. This is because network layer defenses like SWG and email gateways typically rely on two primary methods:
- Block lists of known malicious URLs
- Signatures of known phishing pages
This attack was able to bypass both for the following reasons:
1. Legitimate Hosting Domain
The attackers hosted their phishing page on a legitimate Microsoft hosting domain: windows[.]net.
Windows[.]net is a platform by Microsoft for developers to host .net and Azure web applications. This means the phishing page resided on Microsoft’s own infrastructure. As a result, the page enjoyed high Top-Level-Domain (TLD) reputation.
This made it appear to an outside observer as a legitimate page by Microsoft, and enabled it to bypass traditional URL-based defenses.
Even if a URL-based defense solution did identify malicious activity, it typically wouldn not block the ULR, as blocking all subdomains under `windows.net` would disrupt countless legitimate services hosted by Microsoft, causing operational issues for organizations.
2. Zero-Hour Randomized Subdomains
The attackers made use of randomized subdomains to avoid detection. LayerX labs captured `pushalm83e.z13.web.core.windows[.]net`. However, these domain strings can be easily generated and frequently rotated.
This allows attackers to ensure that the page would not match any existing threat intelligence or URL blacklists in place. This tactic, often referred to as a “zero-hour” technique, allows phishing sites to stay online just long enough to trap victims before they are taken down and rotated to another randomized subdomain.
3. Low Phishing Kit Similarity
The design of the phishing page was novel and did not match existing templates, hashes and signatures commonly seen in phishing kits. This allowed the page to evade detection by solutions relying on phishing page similarity analysis.
Controls relying only on phishing templates and lists, without inspecting the web page contents itself, will be bypassed by advanced and creative attacks.
Nonetheless, despite these characteristics, LayerX was able to detect and block this attack in time.
Why LayerX Detected When Legacy Defenses Failed
Unlike traditional network security tools, that rely primarily on lists of known bad URLs, LayerX protects against phishing and social engineering by leveraging URL filtering with real-time analysis of page behavior.
LayerX’s real-time analysis of web content doesn’t rely solely on domain reputation or static signatures. Instead, it uses an AI-powered neural network to detect risk factors in real-time, even for previously unseen attacks. As a result, when the phishing page attempted to prompt users to enter credentials or call a support number, LayerX’s solution immediately identified this attempt, flagged it as suspicious and automatically blocked the page, preventing potential damage.
LayerX is the first solution that rises up to the challenge of securing the most targeted and exposed attack surface today – the browser, without impacting the user experience.
LayerX delivers comprehensive protection for all web-borne threats with continuous monitoring, risk analysis, and real-time enforcement on any event and user activity in the browsing session.
Enterprises leverage these capabilities to secure their devices, identities, data, and SaaS apps from web-borne threats and browsing risks that endpoint and network solutions can’t protect against. These include blocking data leakage over the web, SaaS apps and GenAI tools, prevention of credential theft from phishing, enforcement of secure access to SaaS resources by the internal or external workforce to mitigate the risk of account takeover, discovery and disablement of malicious browser extensions, Shadow SaaS, and more.
LayerX Enterprise Browser Extension natively integrates with any browser, turning it into the most secure and manageable workspace. Learn more.