What is Phishing?
Phishing is a type of cybersecurity attack in which malicious actors disguise themselves as a trusted person, website or other entity and interact directly with the victim through messages. The bad actors use these messages to obtain sensitive information or deploy malicious software on the victim’s infrastructure.
In an organization, once a phishing attack is successful and one of the employees is compromised, it is easier for the attacker to bypass organizational security perimeters, distribute malware inside a closed environment or gain privileged access to secured company data. This is because the attacker now appears as a trusted and legitimate organizational entity with access privileges.
Phishing is on the Rise
Phishing belongs to the category of Social Engineering, i.e malicious activities accomplished through human interactions. Unfortunately, these kinds of attacks are very popular and are a prominent attack vector in cybercrime. Research conducted by the FBI’s Internet Crime Complaint Center (IC3) found that phishing was one of the most prevalent threats in the US in 2020. Furthermore, according to recent research from IRONSCALES, 81% of organizations around the world have experienced an increase in email phishing attacks between March 2020 and September 2021.
This increase could be a result of the workstyle changes introduced and accelerated by COVID-19. These changes include remote work, an increase in the number of devices workers use (including mobile phones and laptops), a greater reliance on SaaS applications, the browser becoming the primary working tool and office collaboration being shifted to digital communication through email, Microsoft Teams, Slack, etc.
Attackers were quick to adapt. The number of phishing emails spiked by a staggering 667%, according to Barracuda Networks, as attackers lost no time in exploiting the new circumstances of work from home and their increased digital presence. Microsoft’s The New Future of Work report shows similar results, stating that 62% of security professionals say that phishing campaigns were the most increased threat during COVID-19.
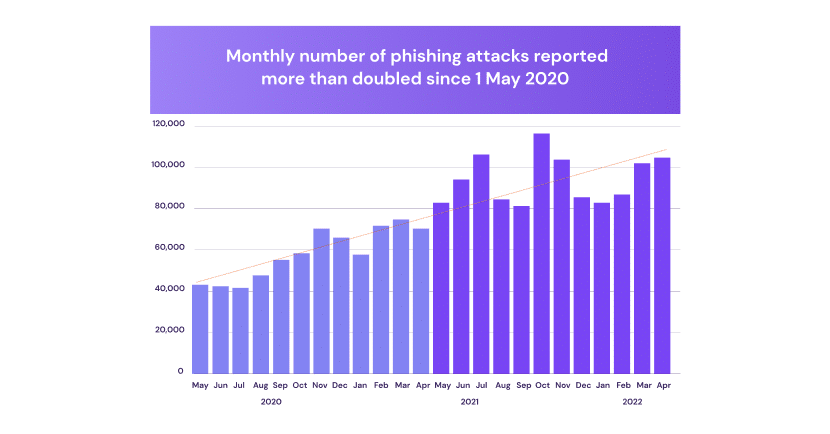
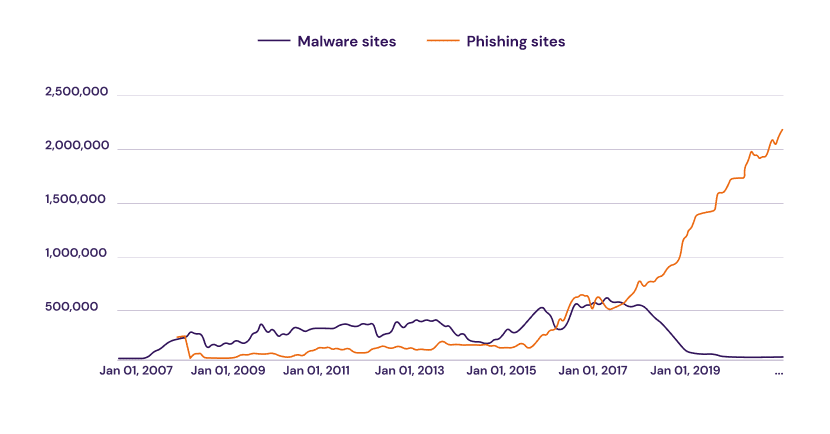
It looks like the number of phishing attacks continues to rise today, even though the pandemic has relatively receded. According to a report by Interisle Consulting Group, the number of phishing attacks grew by 61% between May 2021 and May 2022. In addition, phishing was growing steadily even before the pandemic. As you can see, in this chart by [see graph above], the number of phishing sites has increased over the years compared to the number of malware sites, which has been decreasing since 2017.
These findings are not surprising because phishing continues to drive results for attackers. According to the 2022 Data Breach Investigation Report by Verizon, 2.9% of employees click on phishing emails, a finding they find to be steady over time. We believe this is due to the natural human trait of making mistakes but also to the increased sophistication of phishing attacks, which are able to impersonate legitimate users and websites in highly convincing ways. As cyber security has evolved, attack methods have become cleverer as well.
The Chilling Impact of Phishing
For the individual, a successful phishing attack can result in unauthorized purchases, the stealing of funds, identify theft and personal data loss. For organizations, phishing attacks can target an individual as a way to gain a foothold into organizations. Once breached, organizations are dramatically impacted.
IBM’s 2021 Cost of a Data Breach Report found phishing to be the second most expensive attack vector to contend with, costing organizations an average of $4.65 million. Companies hit by malicious attacks will have to compensate multiple customers and they risk losing investor confidence and general public trust in their product, which has real financial value. For example, following the compromise of Facebook user data in 2018, Facebook’s total value dropped by $36 billion, a loss the company is still recovering from.
Financial loss isn’t the only negative impact that should be taken into consideration. Successful attacks lead to data loss, disruption of critical operations and personal data leakage. These, in turn, could lead to further financial burden of compensating customers or paying regulatory fines for compromising personal data that breaks privacy regulations like GDPR, as well as legal and brand reputation implications.
Phishing Attacks Evade Legacy Security Mechanisms
As the occurrence of phishing attacks expands there seems to be an increase in the sophistication and cleverness of phishing attacks. Today, it is becoming increasingly difficult to stay one step ahead of attackers as they employ ingenious and often highly deceptive phishing techniques in their campaigns.
One prominent example is spear phishing campaigns that easily bypass workplace email security software. For instance, an email scam impersonating Facebook managed to bypass Cisco Email Security Appliance and Microsoft’s Exchange Online Protection. The email was even given Spam Confidence Level (SCL) 1, meaning it managed to skip Microsoft’s spam filters.
A report by Area 1 Security analyzed 1.5 billion messages sent to organizations over a period of six months and found that Office 365 and other well-known SEGs from Cisco, Proofpoint and Mimecast missed over 925,000 phishing emails.
Phishing kits employed by organizations often include traditional evasion mechanisms. However, these old-school cybersecurity solutions fail to recognize different types of evasion and are unable to block phishing attacks, as seen in the examples above.
Here are some examples of mechanisms attackers were able to deploy to overcome security parameters:
MFA Bypass
Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource. For example, a user will need to provide his username and password, then also a pin code that will be sent to the user’s phone. The main benefit of MFA is it will enhance your organization’s security by requiring your users to identify themselves by more than a username and password.
However, MFA is not a bullet-proof solution to prevent phishing attacks. Microsoft has recently uncovered a widespread phishing campaign that bypasses multi-factor authentication (MFA). The initial attack hijacked the Office 365 authentication process, redirecting users to adversary-in-the-middle (AiTM) phishing landing pages aimed at stealing session cookies and credentials. Then, the attackers hijacked a user’s sign-in session and skipped the authentication process even if the user had enabled MFA.
The attackers then used the stolen credentials and session cookies to access affected users’ mailboxes and perform follow-on business email compromise (BEC) campaigns against other targets, as detailed by Microsoft Threat Intelligence Center (MSTIC)
Sandbox Evasion
A sandbox is a security mechanism for separating running programs, and is implemented by executing software or running a web page in a restricted operating system environment. Sandboxing protects from potentially malicious programs or unsafe code by isolating the process from the rest of the organization’s environment. This way, if a threat is detected it does not affect the user’s device.
However, new phishing attacks have been observed to evade this security mechanism. For that purpose they use “Sleepers” – internal stalling mechanisms that a sandbox can’t observe, ensuring the malicious payload will take action only when facing real end-users. This means that the attackers can recognize when they have accessed a real workstation on company infrastructure, and not a sandbox. If there is a sandbox, usually an error will show on the phishing web page and the attack will not commence. As a result, standard security vendors will not classify the phishing website to be malicious, due to the evasion, and the site will continue to operate unnoticed.
Restriction by Device Information
Another evasion technique phishing attacks harness is analyzing device information to root out security vendors that try to disguise themselves as users. Similarly to sandbox evasion, the attackers aim to activate the phishing scheme only when a real user visits the web page.
To do that, threat actors have developed an ability to identify human targets based on different data sources: data from the browser, the operating system, and the way the web page content should be displayed on the user’s screen. With this information, the phishing kit can decide whether the device is used by a person (such as a laptop or phone) or if it is a sandbox or security mechanism disguised as a user.
This information helps the phishing sites classify users based on their screen size or viewport. By accessing visitor data concerning the window height and width of the visitor’s technology, the threat actor knows what type of device the target is using, and can decide whether to attack or evade.
These are only a few examples of an ever-evolving threat landscape, as attackers find new ways every day to bypass conventional cybersecurity protections. This is highly disturbing, and requires a novel approach to the challenges of browser security.
Conventional Solutions Fall Short
As we’ve seen, phishing campaigns have developed mechanisms for detecting conventional anti-phishing software types, be it a sandbox, an email scanner or multi-factor authentication. Once detected by the campaigns, the attackers will deploy a different type of attack and there is little chance the anti-phishing will be effective at blocking or spotting a malicious web page
A Novel Browser-based Approach
The steep rise in the browser’s role in the modern enterprise calls for solutions that protect from cyber attacks prevalent in the browser. Phishing is emerging as the leading threat, in popularity as in severity, of browser borne cyber attacks. Furthermore, conventional anti-phishing software misses many phishing campaigns and lets them go unnoticed, leaving employees and the organization vulnerable.
We believe that an appropriate solution to these problems should be browser based. LayerX Security offers a novel approach for phishing protection.
LayerX browser platform includes a browser extension that monitors browser sessions at the application layer, gaining direct visibility into all browsing events at their post-decryption stage, enabling it to analyze and enforce protective actions in real time with no latency or impact on the user experience. LayerX can seamlessly modify the rendered web page to go beyond crude block\allow access to deliver granular enforcement that neutralizes the malicious aspects of the web page rather than blocking access to it altogether. This is of critical importance in cases when attackers mount their attack on an essentially legitimate page, such as when traversing the DOM structure of a banking app page. LayerX provides the highest level of security without degrading the user’s browsing experience.