Executive Summary
Security researchers at LayerX Security have uncovered a campaign involving malicious VPN and ad-blocking extensions designed to steal sensitive user data. The campaign is persistent in its attempts to resurface, even after it has been taken down previously (more than once). While the extensions part of this reincarnated campaign have 31,000 live installs, past incarnations achieved over 9 million installs, collectively.
Like a kid’s “roly poly” bounce-back toy that keeps standing up, these malicious extensions (and the threat actors behind them) seem intent to keep coming back, no matter how many times they’ve been taken down before. This campaign is a stark reminder of the risks of “free” extensions, and particularly those with access permissions to sensitive data, and the need for defenses to continuously monitor and analyze extensions in an ongoing manner to detect malicious behavior.
Expanded Details:
Free VPN extensions promise privacy, speed, and global access with a single click. For millions of users, they’re an easy way to bypass restrictions or hide IP addresses without paying for a subscription. But that promise often hides a tradeoff: if the product is free, your data becomes the product.
Over the past few years, a group of Chrome extensions advertising “Free Unlimited VPN” services collectively accumulated over 9 million installations. Their names, icons, and descriptions looked perfectly legitimate, and even professional. Yet behind that clean façade, two of these extensions were later revealed to contain deeply invasive code. They were available in the Chrome Web Store for nearly six years before being flagged and removed in May 2025.
Only two months later, a third extension, nearly identical in description, icon style, and internal behavior, appeared in the store. It remains available at the time of writing.
These extensions did far more than proxy network requests. They fetched hidden configuration files from remote servers, altered proxy settings in real time, and intercepted browser navigation events, functioning as remote-controlled proxy redirectors with concealed update channels. What appeared to be a simple free VPN was, in practice, a full browser-level surveillance mechanism.
In this analysis, we’ll describe how these extensions evolved, highlight the technical overlaps between them, and break down the specific techniques used to intercept, redirect, and persist inside the browser. The findings show how permissions such as webRequest, proxy, and declarativeNetRequest can give malicious actors total visibility and control over a user’s browsing traffic.
If installed, these extensions could:
- Intercept and redirect every page you visit.
- Collect browsing data and a list of installed extensions.
- Modify or disable other proxy or security tools.
- Route traffic through attacker-controlled servers, exposing private activity to potential surveillance.
Picture 1: One of the Malicious ‘Free Unlimited VPN’ in store
What follows is a detailed breakdown of their metadata, code behavior, and risks
Table 1: Extension Metadata
| Field | Extension A | Extension B | Extension C |
| Extension ID | foiopecknacmiihiocgdjgbjokkpkohc | bibjcjfmgapbfoljiojpipaooddpkpai | fgpecemjbefkjlcgnhjohdonijdkfooj |
| Display name | VPN Professional – Free Secure and Unlimited VPN Proxy Chrome Extension | VPN-free.pro – Free Unlimited VPN | Free Unlimited VPN |
| Description | Unblock any website and stay secure with VPN Professional. Easy use with one-click activation. VPN Professional – the best VPN! | Unblock any website and stay secure with VPN-free.pro. Easy use with one-click activation. VPN-free.pro – the best VPN! | Unblock any website and stay secure with Free Unlimited VPN. Easy use with one-click activation. Free Unlimited VPN – the best VPN! |
| Support email | admin@free-vpn.pro | support@free-vpn.pro | victorbthomas6@gmail.com |
| Creation date | 21 Sep 2019 | 09 May 2020 | 21 Jul 2025 |
| Last update | 07 Jul 2024 | 14 Feb 2025 | 22 Aug 2025 |
| Deleted from store | 21 May 2025 (removed) | 21 May 2025 (removed) | In store (not removed) |
| Notes | Shares support domain free-vpn.pro with B; removed from store. | Shares support domain free-vpn.pro with A; removed from store. | Different email (Gmail); same wording & icon style; not yet removed. |
While a legitimate browser VPN needs only proxy control with a configuration that is usually static or fetched from a brand-owned, well-known API over HTTPS, the analysis of the described extensions showed remote-controlled configs, dynamic code updates, and full navigation interception, enabling attackers to silently redirect, block, or alter user traffic and change extension behavior after installation.
Technical Deep Dive: Old Version vs New Version
Old version (notable suspicious parts)
Method hijacking
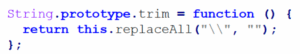
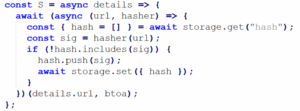
The extension overrides String.prototype.trim to remove backslashes from decoded strings — used to silently de-obfuscate and follow remote URLs.
Remote config fetch (multi-URL config.txt)
The extension periodically fetches a multi-URL config to update behavior and payloads.
Remote PAC install
The extension sets Chrome proxy via pac_script downloaded from remote configuration. By installing a remote PAC script and controlling proxy endpoints, an attacker can route user traffic through servers they control, enabling passive monitoring (logging), active injection (HTML/JS modification), credential theft, or targeted content replacement.
Navigation interception
The extension registers a chrome.webRequest.onBeforeRequest listener for “<all_urls>” targeting main-frame requests, allowing the extension to intercept every page load and redirect tabs to destinations defined in its remote configuration.
Dynamic DNR updates
The extension uses declarativeNetRequest.updateDynamicRules to change filtering/routing on the fly.
History tampering:
The extension uses history.replaceState(“”, “”, ‘https://${location.host}’) to remove traces of original redirect URLs.
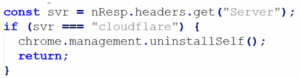
Server-driven uninstall
The extension triggers self-uninstall based on a remote server (“Cloudflare”) check which is used to evade analysis or targeted takedown.
Permission check & self-remove
In case the <all_urls> permission was removed, the extension uninstalled itself.
Service worker persistence
The extension injects a keepalive script into tabs to keep the background worker alive (evade MV3 unloads).
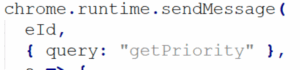
Priority messaging
The extension sends messages to other extensions to obtain priority over navigation.
Fake UX settings
The extension stores country/version/uid but no real local VPN tunnel code, likely a cosmetic or server-driven choices.
2025 version
The new version published on 21 Jul 2025, is notably more advanced and evasive than the old one: it removes some overtly suspicious code while adding stealthier mechanisms, such as delayed proxy activation, dynamic code downloads, and the ability to disable other extensions, making it harder to detect yet granting even greater remote control over the user’s browser and traffic. The notable suspicious parts are:
Remote multi-URL config fetch
As its older version extensions, this one also periodically fetches a multi-URL config to update behavior and payloads.
Remote PAC script
The extension sets Chrome proxy via pac_script downloaded from remote configuration which routes traffic through attacker servers, but in newer version PAC contains a two seconds delay before activation which is likely used for sandbox evasion. Additionally, the core proxy routing logic, including setup and configuration variables, is downloaded at runtime and executed dynamically.
Navigation interception
The extension registers a chrome.webRequest.onBeforeRequest listener for “<all_urls>” targeting main-frame requests, allowing the extension to intercept every page load and redirect tabs to destinations defined in its remote configuration.
Dynamic DNR updates
The extension uses declarativeNetRequest.updateDynamicRules to change filtering/routing on the fly.
Service worker persistence
The extension injects a keepalive script into tabs to keep the background worker alive (evade MV3 unloads).
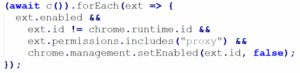
Disables other proxy extensions
The extension scans for other extensions with proxy permissions and if found disables them, giving exclusive routing control.
Exfiltration
The extension enumerates installed extensions and sends a list to the remote server.
URL hashing & upload
The extension hashes visited URLs and periodically sends them to C2 for profiling and targeting.
Risk & impact
- Complete traffic interception: By installing a remote PAC script and controlling proxy endpoints, an attacker can route user traffic through servers they control, enabling passive monitoring (logging), active injection (HTML/JS modification), credential theft, or targeted content replacement.
- Selective, stealthy redirection: With onBeforeRequest + DNR updates, the operator can land victims on phishing pages, steered download pages, or ad farms, and then change payloads later without user interaction.
- Persistent remote control: Runtime code/config fetch + DNR updates + keepalive injection allow operator to change extension behavior post-install, bypassing store review after initial publication.
- Evasion of analysis & traces: timing gates (2s direct traffic), history.replaceState, dynamic uninstall on detection. These tactics all reduce forensic evidence and sandbox detection.
- Attack surface expansion: disabling other proxy extensions or enumerating installed extensions allows targeted disabling of defensive tools.
- Privacy & profiling: collecting hashed URLs, extension lists, and potentially cookies/session tokens (if proxied to attacker servers) is a severe privacy breach and can enable targeted follow-on attacks.
Conclusion
These extensions show how easily a trusted browser add-on can evolve into a remote-controlled proxy system: over six years, two nearly identical “free VPN” extensions silently redirected traffic, updated their behavior through hidden configuration channels, and exfiltrated user data before removal, only for a third clone to appear two months later, demonstrating that even tools marketed for privacy can become long-lived instruments of surveillance when granted broad permissions and minimal scrutiny.
It’s worth mentioning that during our investigation, we discovered six additional, almost identical extensions. However, these were adblockers and music downloaders.
IOCs
Extension IDs – Current Live Extensions
- fgpecemjbefkjlcgnhjohdonijdkfooj – active – 30,000 Users (Chrome)
- kekfppnajjchccpkfaogiomfcncbgagc – 131,445 Users (Edge)
- nhiafglcjghpmcipelflfhkckdpcokid – active – 1,000 Users
- hfofhoffdcfcjgmilkpnhkamcgemaban – 100,000 Users
Extension IDs of Past Extensions (no longer live):
- foiopecknacmiihiocgdjgbjokkpkohc – 100,000 Users
- bibjcjfmgapbfoljiojpipaooddpkpai – 9,000,000 Users
- ngahaphlngmdfhbhkplbglnfhehnpgdb – 100,000 Users
- ibibeegnncapfdcgpdnnbjbbojglhlmk – 20,000 Users
- anlhakiodmebohjmkbciohpglnjifjaa – 5,000 Users
Support emails / domains
- admin@free-vpn.pro
- support@free-vpn.pro
- victorbthomas6@gmail.com
- okmusic.pro@yandex.ru
- support@adsblocker.top
- facebook@adscleaner.top
- andreylebedev.ext@gmail.com
- support@yandexmusic.pro
- free-vpn.pro
- okmusic.cyou
- dialspeed.xyz
- adsblocker.top
- facebook.adscleaner.top
- vpn-professional.company
- procompany.top
- proffconfig.top
- configapp.top
- yandexmusic.pro
- configanalytics.icu
Names / branding
- “VPN Professional – Free Secure and Unlimited VPN Proxy Chrome Extension”
- “VPN-free.pro – Free Unlimited VPN”
- “Free Unlimited VPN”
- “VPN Professional – Free Unlimited VPN Proxy”
- “Ads Blocker”
- “OKmusic – скачать музыку и видео Одноклассники | OK.ru Music Downloader”
- “Ads Cleaner for Facebook”
- “Speed Dial | Bookmarks | New Tab Page | Quick Access | Custom Search”
- “Скачать музыку” (“Download Music”)
Remediation & Mitigation
Immediate actions for end users:
- Uninstall any extension matching the IOCs above.
- Clear browser cookies, local storage, and any stored credentials that may have been captured while the extension was active.
- Rotate passwords for sensitive accounts (especially if you used the browser for logins while the extension was active).
- Run an anti-malware/anti-adware scan locally.
Enterprise / SOC actions:
- Block identified support domains and C2 hosts at the network perimeter (DNS + proxy + firewall) while investigating.
- Query telemetry for extension installs and PAC changes (EDR/MDM: look for registry or preference modifications used to set PACs).
- Revoke sessions for critical services if any traffic was proxied through attacker hosts.
- Notify users and require reinstallation of browsers or profile resets for impacted endpoints as necessary.
- Report the extension(s) to the Chrome Web Store with detailed IOCs and supporting evidence.