Contributors: Dar Kahllon
As generative AI tools like ChatGPT, Claude, Gemini, and Grok become part of everyday workflows, attackers are increasingly exploiting their popularity to distribute malicious browser extensions.
In this research, we uncovered a coordinated campaign of Chrome extensions posing as AI assistants for summarization, chat, writing, and Gmail assistance. While these tools appear legitimate on the surface, they hide a dangerous architecture: instead of implementing core functionality locally, they embed remote, server-controlled interfaces inside extension-controlled surfaces and act as privileged proxies, granting remote infrastructure access to sensitive browser capabilities.
Across 30 different Chrome extensions, published under different names and extension IDs and affecting over 260,000 users, we observed the same underlying codebase, permissions, and backend infrastructure.
Critically, because a significant portion of each extension’s functionality is delivered through remotely hosted components, their runtime behavior is determined by external server-side changes, rather than by code reviewed at install time in the Chrome Web Store.
Campaign Structure and Impact
The campaign consists of multiple Chrome extensions that appear independent, each with different names, branding, and extension IDs. In reality, all identified extensions share the same internal structure, JavaScript logic, permissions, and backend infrastructure.
Across 30 extensions impacting more than 260,000 users, the activity represents a single coordinated operation rather than separate tools. Notably, several of the extensions in this campaign were Featured by the Chrome Web Store, increasing their perceived legitimacy and exposure.
This technique commonly known as extension spraying, is used to evade takedowns and reputation-based defenses. When one extension is removed, others remain available or are quickly re-published under new identities. Although the extensions impersonate different AI assistants (Claude, ChatGPT, Gemini, Grok, and generic “AI Gmail” tools), they all serve as entry points into the same backend-controlled system.
Technical Overview
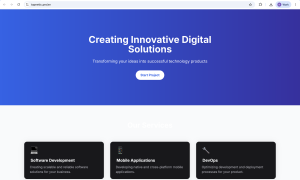
In this report we will analyze the AI Assistant (nlhpidbjmmffhoogcennoiopekbiglbp) extension.
Figure 1. Featured “Claude” Assistant
Remote Iframe as the Core UI
The extension renders a full-screen iframe pointing to a remote domain (claude.tapnetic.pro). This iframe overlays the current webpage and visually appears as the extension’s interface.
Figure 2. IFrame Injection
Because the iframe loads remote content:
- The operator can change UI and logic at any time
- No Chrome Web Store update is required
- New capabilities can be introduced silently
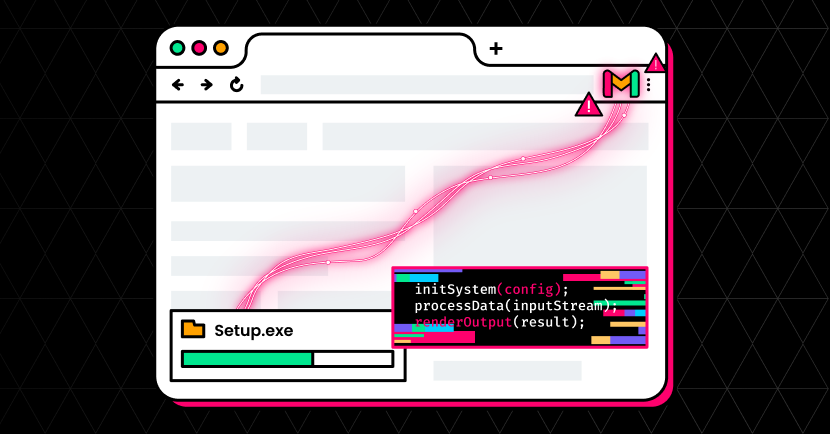
Page Content Extraction
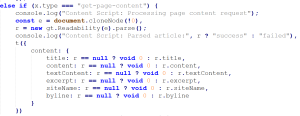
When instructed by the iframe, the extension queries the active tab and invokes a content script that extracts readable article content using Mozilla’s Readability library. The extracted data includes titles, text content, excerpts, and site metadata.
Figure 3. Page Content Extraction
This information is then sent back to the remote iframe, meaning that a third-party server can receive structured representations of any page the user is viewing, including sensitive internal or authenticated pages.
Voice Recognition Capability
The extension also supports message-triggered voice recognition using the Web Speech API. Upon request from the iframe, speech recognition is started and the resulting transcript is returned to the remote page.
While browser permissions may limit abuse in some cases, the presence of this capability demonstrates the broad scope of access granted to the remote controller.
Telemetry Collection
The extension package includes explicit tracking pixel scripts that send install and uninstall events to a third-party analytics endpoint.
These mechanisms are commonly associated with:
- Attribution tracking
- Monetization funnels
- Retention analysis
Gmail Integration Cluster
A subset of the campaign, comprising 15 extensions, explicitly targets Gmail. Despite being published under different names and branding, and marketed as offering distinct capabilities not always related to email assistance, all of these extensions share an identical Gmail integration codebase.
Each includes a dedicated Gmail-only content script that runs at document_start on mail.google.com, separate from the generic <all_urls> content script. This module injects extension-controlled UI elements into Gmail and maintains persistence using MutationObserver and periodic polling.
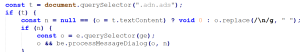
The Gmail integration reads visible email content directly from the DOM, repeatedly extracting message text via .textContent from Gmail’s conversation view.
Figure 4. Gmail Content Reading
This includes email thread content and, depending on state, draft or compose-related text.
When Gmail-related features such as AI-assisted replies or summaries are invoked, the extracted email content is passed into the extension’s logic and transmitted to third-party backend infrastructure controlled by the extension operator. As a result, email message text and related contextual data may be sent off-device, outside of Gmail’s security boundary, to remote servers.
C&C -Infrastructure and Threat Attribution
tapnetic[.]pro C&C Domain Characteristics
All analyzed extensions communicate with infrastructure under the tapnetic[.]pro domain. While the domain hosts a publicly accessible website that appears legitimate at first glance, our analysis found that:
- The website presents generic marketing-style content
- No features, downloads, or user actions are actually functional
- No clear product, service, or ownership information is provided
At the time of analysis, the site appeared to function primarily as cover infrastructure, lending legitimacy to the domain while the real activity occurs through extension-controlled subdomains.
Figure 5. Tapnetic.pro
Subdomain Segmentation
Each extension communicates with a dedicated subdomain of tapnetic[.]pro, typically themed to match the impersonated AI product (e.g., Claude, ChatGPT, Gemini).
Figure 6. Tapnetic.pro subdomains – VirusTotal.com
This design provides several advantages to the operator:
- Logical separation between extensions
- Reduced blast radius if a single subdomain is blocked
- Easier rotation or replacement of individual extension backends
Despite different subdomains, request structure, parameters, and server behavior are consistent across the campaign, indicating a single backend system.
Extension Lifecycle Abuse and Re-Upload Evasion
We also observed active evasion of Chrome Web Store enforcement.
One extension in the campaign, fppbiomdkfbhgjjdmojlogeceejinadg, was removed from the Chrome Web Store on February 6, 2025.
Less than two weeks later, an identical extension was published under a new ID and name:
- New extension ID: gghdfkafnhfpaooiolhncejnlgglhkhe
- Upload date: February 20, 2025
The re-uploaded extension is a full copy of the removed one:
- Identical JavaScript logic
- Same permissions
- Same iframe-based architecture
- Same tapnetic.pro infrastructure
This behavior is consistent with extension spraying tactics, allowing operators to quickly restore distribution after takedowns while maintaining the same backend control.
Conclusion
By leveraging the trust users place in well-known AI names such as Claude, ChatGPT, Gemini, and Grok, attackers are able to distribute extensions that fundamentally break the browser security model.
The use of full-screen remote iframes combined with privileged API bridges transforms these extensions into general-purpose access brokers, capable of harvesting data, monitoring user behavior, and evolving silently over time. While framed as productivity tools, their architecture is incompatible with reasonable expectations of privacy and transparency.
As generative AI continues to gain popularity, defenders should expect similar campaigns to proliferate. Extensions that delegate core functionality to remote, mutable infrastructure should be treated not as convenience tools, but as potential surveillance platforms.
Indicators of Compromise (IOCs)
Extensions
| ID | Name | Installs |
| nlhpidbjmmffhoogcennoiopekbiglbp |
AI Assistant |
50,000 |
| gcfianbpjcfkafpiadmheejkokcmdkjl |
Llama |
147 |
| fppbiomdkfbhgjjdmojlogeceejinadg |
Gemini AI Sidebar |
80,000 |
| djhjckkfgancelbmgcamjimgphaphjdl |
AI Sidebar |
9,000 |
| llojfncgbabajmdglnkbhmiebiinohek |
ChatGPT Sidebar |
10,000 |
| gghdfkafnhfpaooiolhncejnlgglhkhe |
AI Sidebar |
50,000 |
| cgmmcoandmabammnhfnjcakdeejbfimn |
Grok |
261 |
| phiphcloddhmndjbdedgfbglhpkjcffh |
Asking Chat Gpt |
396 |
| pgfibniplgcnccdnkhblpmmlfodijppg |
ChatGBT |
1,000 |
| nkgbfengofophpmonladgaldioelckbe |
Chat Bot GPT |
426 |
| gcdfailafdfjbailcdcbjmeginhncjkb |
Grok Chatbot |
225 |
| ebmmjmakencgmgoijdfnbailknaaiffh |
Chat With Gemini |
760 |
| baonbjckakcpgliaafcodddkoednpjgf |
XAI |
138 |
| fdlagfnfaheppaigholhoojabfaapnhb |
Google Gemini |
7,000 |
| gnaekhndaddbimfllbgmecjijbbfpabc |
Ask Gemini |
1,000 |
| hgnjolbjpjmhepcbjgeeallnamkjnfgi | AI Letter Generator | 129 |
| lodlcpnbppgipaimgbjgniokjcnpiiad | AI Message Generator | 24 |
| cmpmhhjahlioglkleiofbjodhhiejhei | AI Translator | 194 |
| bilfflcophfehljhpnklmcelkoiffapb | AI For Translation | 91 |
| cicjlpmjmimeoempffghfglndokjihhn | AI Cover Letter Generator | 27 |
| ckneindgfbjnbbiggcmnjeofelhflhaj | AI Image Generator Chat GPT | 249 |
| dbclhjpifdfkofnmjfpheiondafpkoed | Ai Wallpaper Generator | 289 |
| ecikmpoikkcelnakpgaeplcjoickgacj | Ai Picture Generator | 813 |
| kepibgehhljlecgaeihhnmibnmikbnga | DeepSeek Download | 275 |
| ckicoadchmmndbakbokhapncehanaeni | AI Email Writer | 64 |
| fnjinbdmidgjkpmlihcginjipjaoapol | Email Generator AI | 881 |
| gohgeedemmaohocbaccllpkabadoogpl | DeepSeek Chat | 1,000 |
| flnecpdpbhdblkpnegekobahlijbmfok | ChatGPT Picture Generator | 251 |
| acaeafediijmccnjlokgcdiojiljfpbe | ChatGPT Translate | 30,000 |
| kblengdlefjpjkekanpoidgoghdngdgl | AI GPT | 20,000 |
| idhknpoceajhnjokpnbicildeoligdgh | ChatGPT Translation | 1,000 |
| fpmkabpaklbhbhegegapfkenkmpipick | Chat GPT for Gmail | 1,000 |
Domains
Tapnetic[.]pro
onlineapp[.]pro
Emails
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
Tactics, Techniques, and Procedures (TTPs)
| Tactic | Technique |
| Resource Development | LX2.003(T1583) – Acquire Infrastructure |
| Initial Access | LX3.004 (T1189) – Drive-by Compromise |
| Initial Access | LX3.003 (T1199) – Trusted Relationship |
| Execution | LX4.003 – Script Execution |
| Defense Evasion | LX7.011 (T1036) – Masquerading |
| Credential Access | LX8.007(T1557) – Adversary-in-the-Middle |
| Collection | LX10.012 – Web Communication Data Collection |
| Collection | LX10.005 – Collect User’s Information |
| Command and Control | LX11.004 – Establish Network Connection |
| Command and Control | LX11.005 – Web Service-Based C2 |
| Exfiltration | LX12.001 – Data Exfiltration |
Recommendations
Security professionals, enterprise defenders, and browser developers should take the following actions:
- Audit extensions within managed environments, especially those installed outside of policy controls.
- Deploy behavior-based extension monitoring technologies to detect unauthorized network activity or suspicious DOM manipulation.
- Strengthen runtime monitoring and enforcement, not just install-time review, to detect post-installation behavior changes driven by backend infrastructure.