In the modern corporate environment, web browsers have become indispensable tools for daily operations. Recent studies indicate that the average employee spends over 85% of their workday using a browser. This heavy reliance on browsers, while enhancing productivity, also introduces significant security challenges, particularly concerning fileless data movement.
As security and DLP experts face daily challenges, preventing copy-pastes is an impossible task with today’s DLP tools. Imagine the following scenarios-
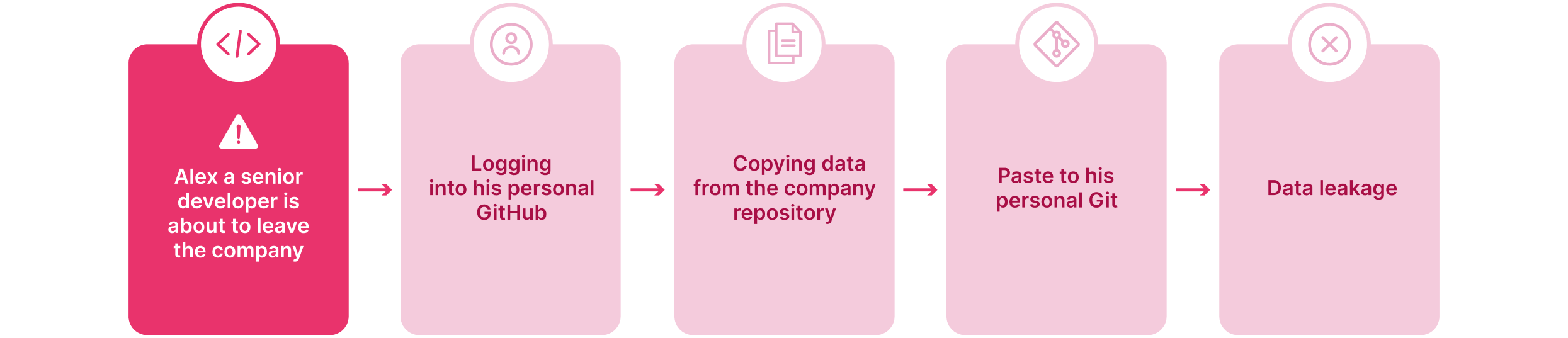
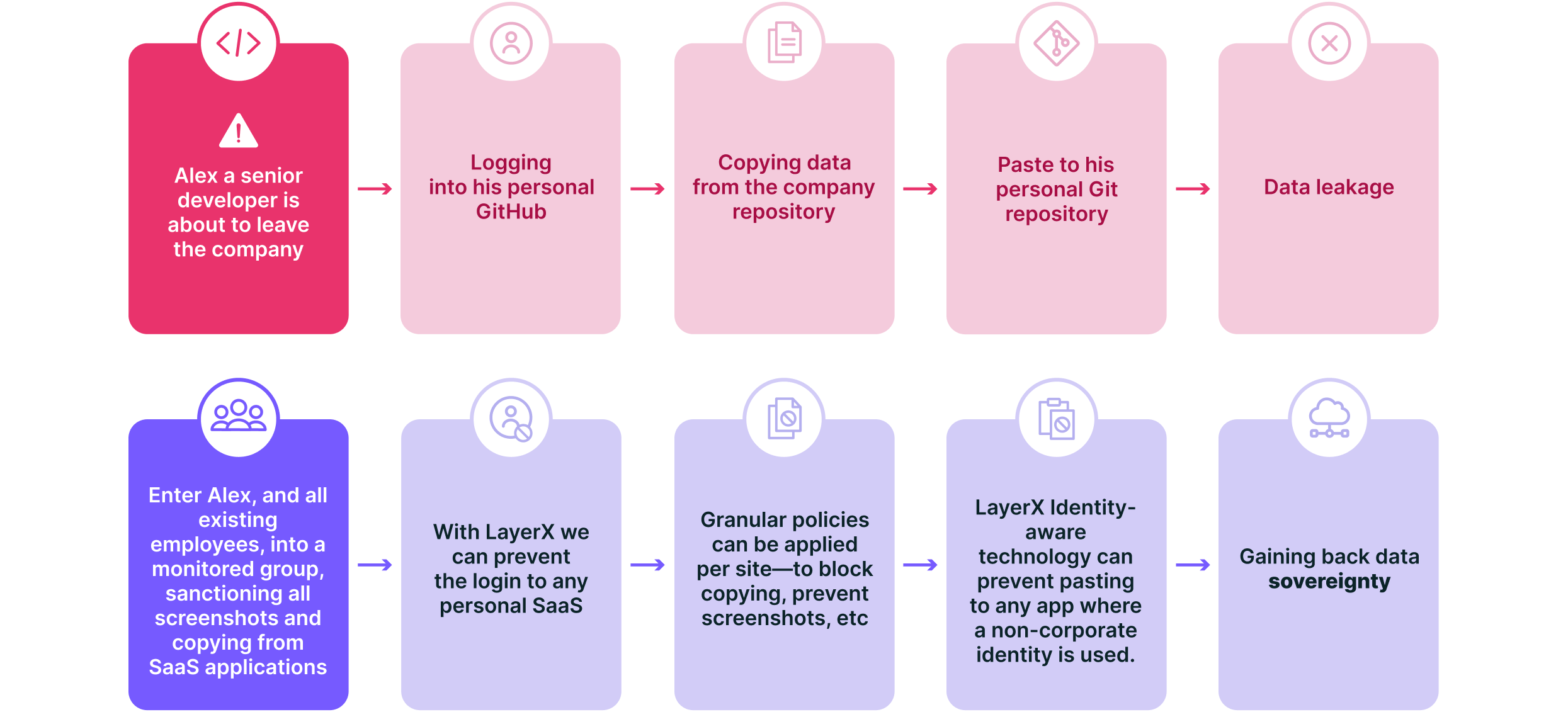
1- Jessica, a developer, is about to leave for a competitor. Instead of triggering security alerts with downloads, she copy-pastes critical code snippets into her personal GitHub repository. Within minutes, proprietary data is outside company control—undetected by traditional DLP tools.
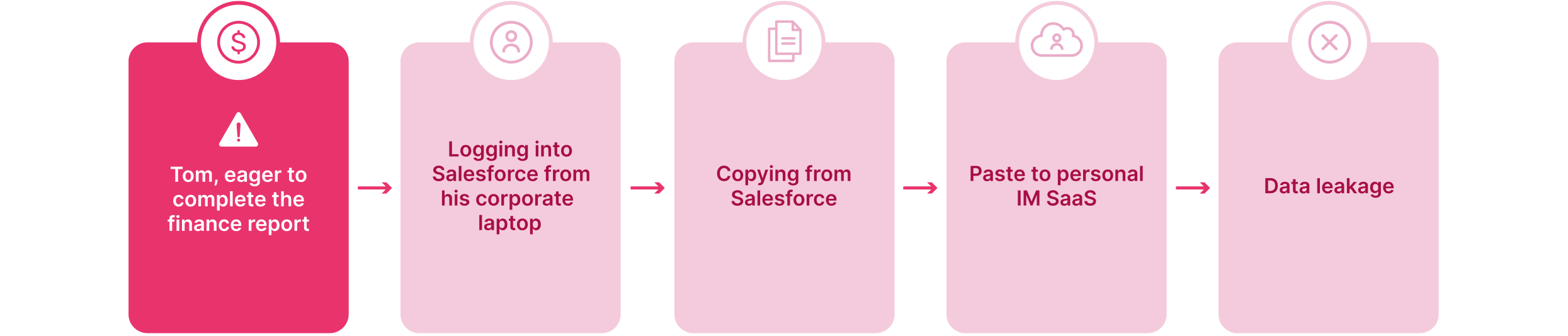
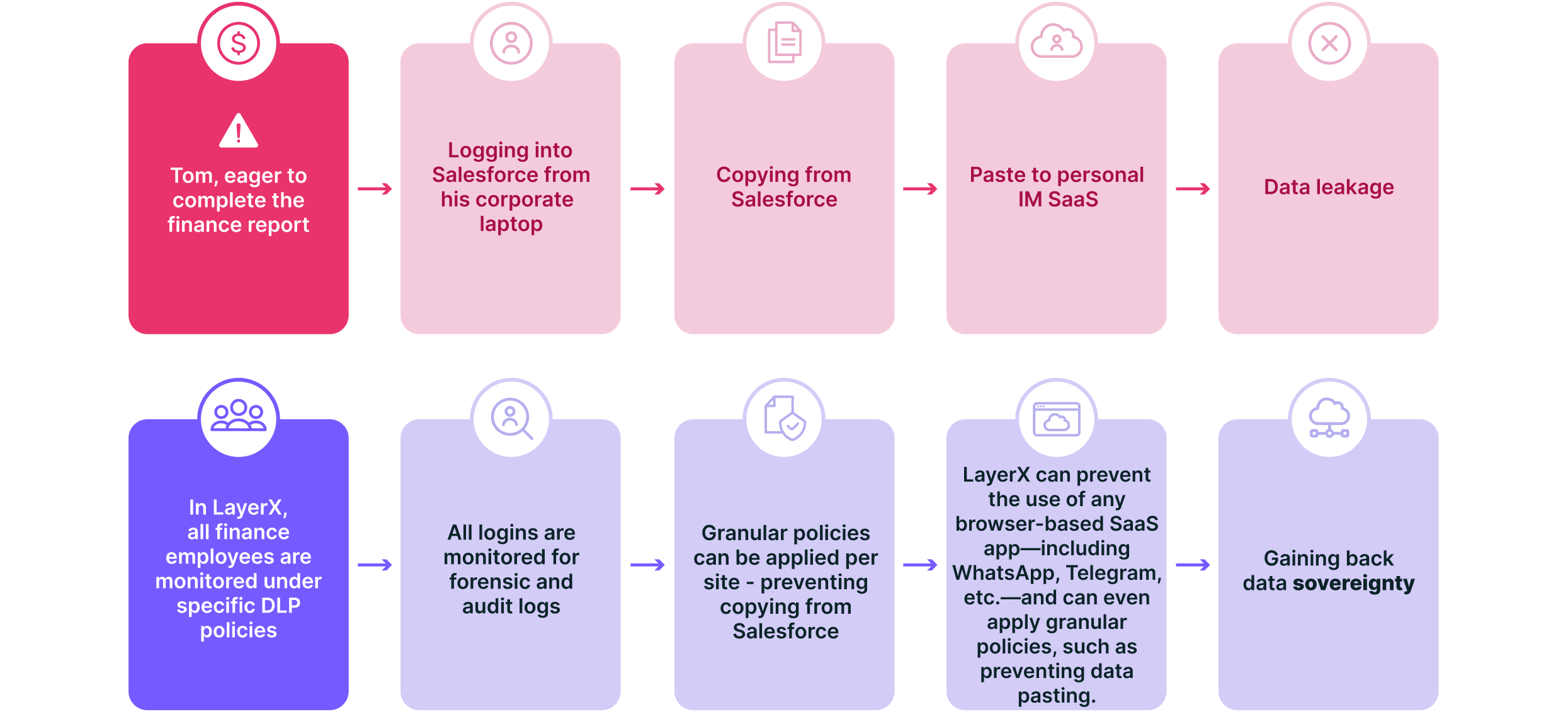
2- Tom, a finance employee, is trying to complete his year-end financial report. However, due to company security policies, he cannot download the necessary reports from Salesforce. Frustrated, he copies several lines of the financial data—including revenue figures, major deals, and sensitive customer details—and sends them via his WhatsApp/Signal/Telegram. No security alerts are triggered, and the company remains unaware of this major data exfiltration risk.
How can you prevent this in your organization?
The Growing Threat of Fileless Data Movement
These cases highlight the risks of fileless data movement, where data exfiltration occurs through browser-based actions like copy-pasting, typing, or unauthorized sharing via messaging apps. Since these actions don’t trigger file-based security events, traditional DLP tools fail to detect them, leaving organizations vulnerable to data leaks. Even on authorized SaaS apps, typing and copy-pastes cannot be detected or provisioned. Leaving all the companies from all sectors with less sovereignty over their most valuable data.
The Fileless Data Problem Multiplies With The Growth of Shadow SaaS
While on authorized SaaS apps, companies can apply some policies, the rise of shadow SaaS further exacerbates the DLP issues, as almost no tool can sanction the fileless data movement there. Employees frequently use unauthorized SaaS applications, often accessed through browsers, without the knowledge or approval of IT departments. This practice not only circumvents established security protocols but also increases the risk of data leaks. Traditional DLP solutions, which focus on sanctioned applications and known data channels, struggle to monitor and control data flow within these unsanctioned platforms.
Why Other Security Solutions Won’t Cover It
Many existing security solutions are ineffective against fileless data movement because they are designed for traditional data exfiltration methods:
- Endpoint DLP: Primarily focused on file-centric monitoring, but in these cases, no actual file event has taken place.
- EDR/XDR: These solutions detect and mitigate malicious activity, but the actions described here (copy-pasting) are legitimate user activities that should only be restricted in specific contexts.
- Network Solutions: While network security tools can block access to malicious sites, the sites being used (such as personal Git repositories, AI tools, or cloud storage services) are legitimate. Moreover, network solutions lack visibility into browser session activities, missing last-mile user behavior that leads to data leaks.
Now What?
The first step is understanding that browser DLP and security are not nice-to-haves anymore and shifting the data protection strategies. Unlike legacy solutions, LayerX provides real-time, browser-native protection that prevents data loss and can sanction data movement to Shadow SaaS.
Let’s take our 2 scenarios and see how LayerX’s robust solution can protect data at all stages of leakage and restore the organization’s data sovereignty.
Scenario 1 –
Scenario 2 –
Unlike legacy solutions, LayerX provides real-time, browser-native protection that prevents data loss at the source – even for fileless data, even from shadow SaaS
✅ Monitor and Control Data Flows—Detects and blocks unauthorized copy-paste, typing, downloading, printing and sharing of sensitive data (PII, PI and IP).
✅ Identity-aware and Shadow SaaS—LayerX policy detects and prevents fileless data from being shared outside of the organization’s approved apps and services.
✅ Additional protection to the approved SaaS- LayerX can add protections to your approved apps. For example, preventing copying from your CRM, financial apps, etc.
✅ Seamless, Frictionless Security – No impact on user experience, ensuring security without productivity loss.