95% of organizations report browser-based attacks.
Most don’t have a plan to stop them.
That’s not a throwaway stat. It’s a signal that security strategies are misaligned with where the work, and the risk, actually happen.
Today, the browser is where data moves. Where decisions happen. Where attackers hide.
So why do most security stacks stop right before it?
In The Secure Enterprise Browser Maturity Guide: Safeguarding the Last Mile of Enterprise Risk, cybersecurity strategist Francis Odum introduces a practical model for finally securing the browser, the most overlooked layer in the enterprise.
Your Browser Is the One Place Your Stack Doesn’t See
Let’s start with a number that reframes the entire problem: 85% of the modern workday now takes place inside a browser. That means every login, every document, every dashboard, every GenAI prompt, every sensitive customer detail, all accessed and manipulated in-browser.
And yet:
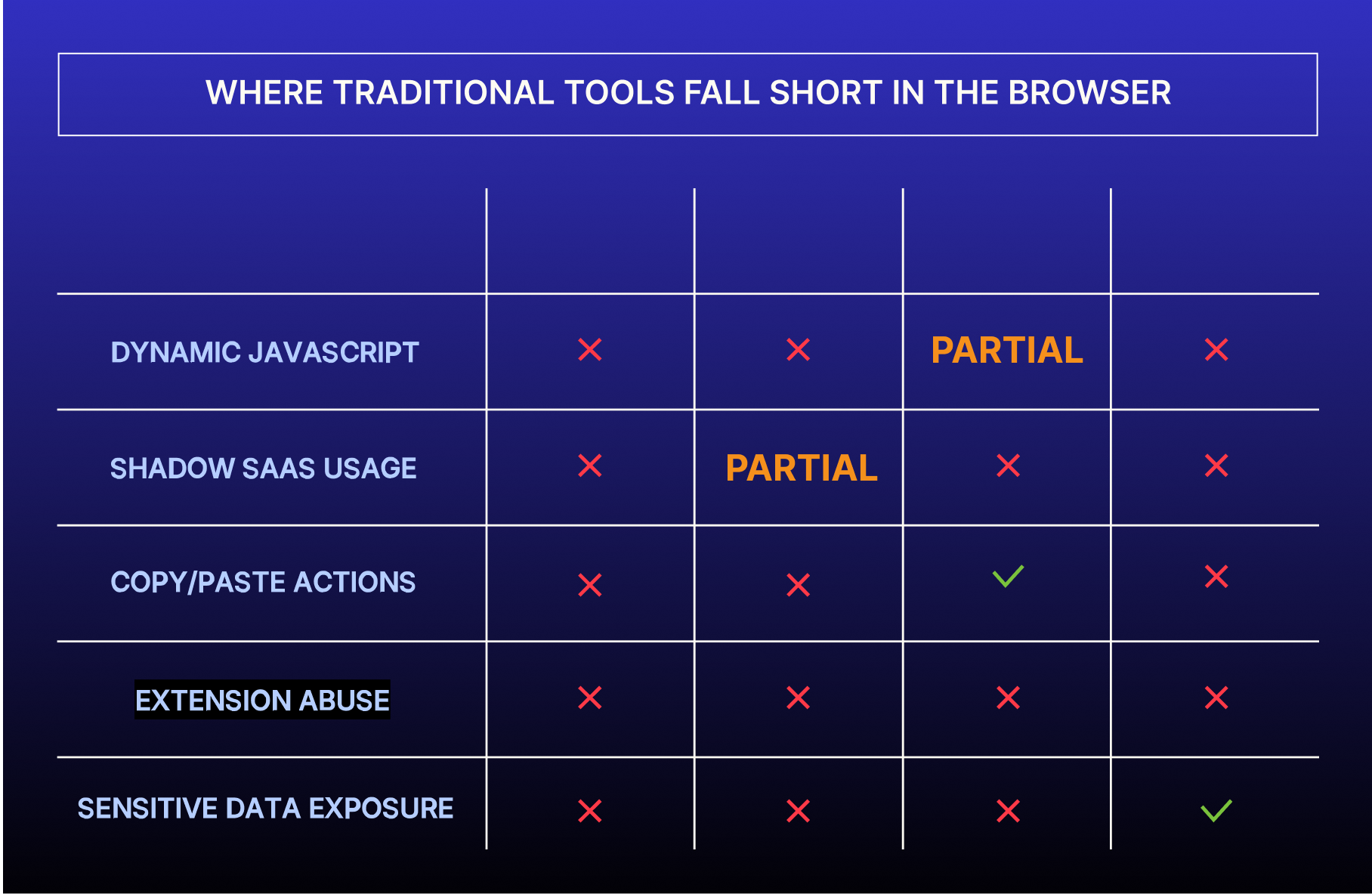
- EDR watches the OS, not the DOM.
- CASB sees only sanctioned apps, not what’s really in use.
- DLP can’t inspect copy/paste or keystrokes inside the browser.
- SWGs block known bad domains, not dynamic SaaS, not extensions, not GenAI tools.
The result?
Real enterprise risk, fileless, fast, and user-triggered, goes completely undetected. Until it’s too late.
We’ve seen this firsthand: PII pasted into an AI chatbot, business files uploaded to personal accounts, credential cookies exfiltrated by extensions. And all of it invisible to the stack that was supposed to “see everything.”
The Guide That Finally Gives CISOs a Way to Fix It
Francis Odum’s Secure Enterprise Browser Maturity Guide offers something security teams desperately need: a framework.
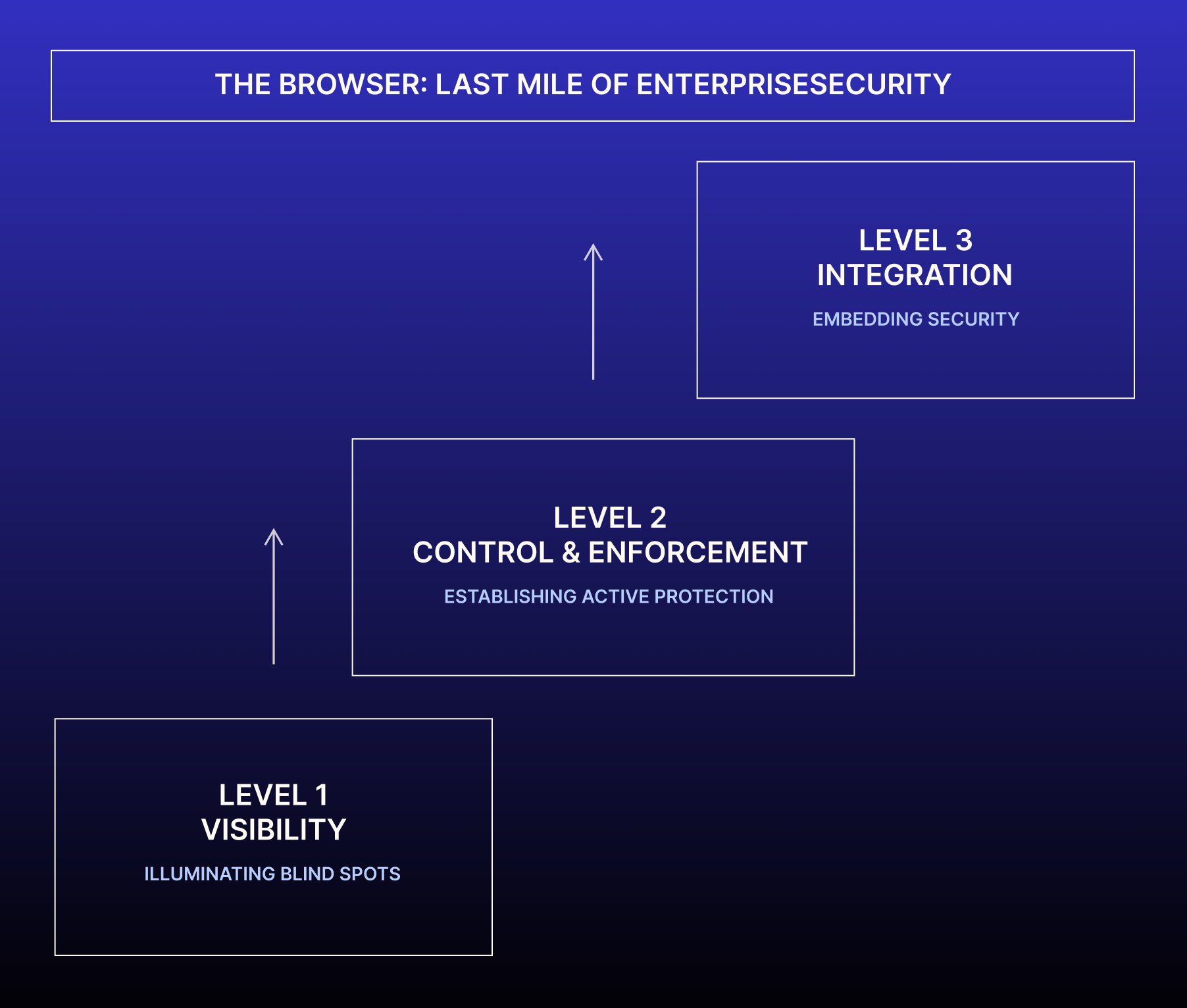
The model outlines three stages of browser-layer maturity, each grounded in observable challenges and built for real-world environments.
Stage 1: Visibility
It starts with a deceptively simple question: Do you even know what’s happening in your browsers?
For most orgs, the answer is no.
They don’t know what extensions are installed, which SaaS tools are being accessed, where sensitive data is being pasted or uploaded, or whether the browser is running on a corporate or unmanaged device.
Stage 1 is about making the invisible visible.
That includes:
- Inventorying browser types and versions
- Capturing in-browser telemetry (not just traffic logs)
- Seeing what users are copying, pasting, and uploading
- Surfacing shadow SaaS and GenAI usage before it creates exposure
We often hear from teams who believe they already have this visibility through CASB or SWG. But these tools weren’t designed for the browser itself. They operate around it, not within it.
This stage is where maturity begins, and where most security teams finally realize how deep the gap really is.
Stage 2: Control & Enforcement
Once you can see the risk, the next question is: Can you stop it?
In this phase, the focus shifts to actively managing browser-based behavior, without turning the browser into a productivity dead zone.
The guide outlines key enforcement strategies, like:
- Blocking uploads/downloads between specific apps and untrusted destinations
- Controlling or removing risky browser extensions
- Enforcing identity-aware session rules (e.g., stopping personal Gmail access in a corporate tab)
- Intercepting copy/paste of sensitive data
- Prompting users with real-time warnings before risky actions
What’s critical here is timing. Most traditional controls act after the event, after the file is sent, after the data is exposed.
Browser-native enforcement means stopping the action in the moment. Before the paste. Before the upload. Before the breach.
That’s where the game changes.
Stage 3: Integration & Usability
This is where security becomes mature, usable, and sustainable.
By this stage, browser-layer controls don’t live in a silo. They feed into SIEM, XDR, IAM, and ZTNA policies. They influence risk scores and trigger automated incident response. They support dual profiles to separate personal from work browsing. They cover contractors, unmanaged devices, third-party users, at scale.
Most importantly, they do all of this without slowing people down.
At LayerX, we’ve seen the most successful teams treat the browser like a control plane, not a black box. They make it part of their broader security architecture, not a bolt-on.
And it works.
We’ve watched companies detect and block a GenAI prompt leak in real time. Prevent a rogue extension from harvesting credentials. Shut down unsanctioned app usage, all without disrupting workflows.
GenAI: The Last-Mile Stress Test
If browser risk wasn’t already obvious, GenAI made it unavoidable.
Employees are pasting customer records, source code, strategic plans into LLMs like ChatGPT and Bard, without any policy, protection, or even awareness.
According to the guide, 65% of organizations have zero control over what data is being fed into GenAI tools. And since prompts look like keystrokes, not files, traditional DLP can’t stop them. Prompts are essentially unsanctioned API calls, with no audit trail.
That means GenAI isn’t just a risk. It’s a visibility collapse. And the browser is the only logical enforcement point.
The maturity model addresses this head-on, showing exactly how to detect and stop risky GenAI interactions at the point of use, not after the data is already gone.
What Makes This Model Work
What we love about this guide is that it’s not theoretical. It’s actionable.
It gives teams:
- Clear indicators to benchmark where they are today
- Tactics for quick wins (like audit-mode telemetry, extension discovery)
- A phased roadmap to reach full maturity
- Rollout guidance that accounts for change management and stakeholder alignment
And perhaps most importantly, it doesn’t ask you to rip and replace what you’ve already built.
You don’t need to abandon your SSE deployment or DLP strategy. You just need to extend them into the one layer they can’t see.
The New Control Layer
We believe this guide should be mandatory reading for any CISO with SaaS, BYOD, or GenAI risk on their radar.
It validates what we’ve seen on the frontlines: That the browser is no longer just a place where work gets done. It’s where data exposure begins. And if your controls don’t extend into that layer, your security program stops one step too soon.
Whether you’re just starting to audit extensions, or building toward full browser-native policy enforcement, this framework helps you do it strategically, and communicate your progress to leadership.
You Can’t Secure What You Don’t See
Security architecture has evolved to protect where data lives. But to protect where it moves, copy, paste, prompt, upload, we need to rethink the last mile.
This guide shows how.