New research by LayerX shows that new AI browsers, and particularly Perplexity’s Comet browser and Genspark, exhibit alarmingly low success rates in blocking even poorly crafted and obviously malicious phishing websites.
These findings, based on research by LayerX security researcher Paloma Perlov, are crucial as they expose a new and expanding threat surface of AI browsers. The implications are that without proper security safeguards, users of AI browsers are at a disproportionately higher risk of falling victim to phishing and web attacks, which could take advantage of the built-in AI engine to steal users’ credentials and private data.
AI Browsers are a New Control Point for AI
AI browsers are an emerging interface for AI usage. A new generation of AI browsers, such as Comet (by Perplexity), Dia (by the makers of Arc browser), Genspark, Edge Copilot, as well as upcoming browsers by Opera (Neon) and a rumored AI browser by OpenAI, is integrating AI directly into the day-to-day browsing experience. However, this new work interface also creates a new threat surface which bad actors can exploit in order to steal user credentials and data.
New technical research by LayerX has found that new AI browsers are disproportionately exposed to phishing and web attacks, compared to traditional non-AI browsers. “Leading” the pack of AI browsers in terms of vulnerability were Comet and Genspark browsers, which allowed over 90% of compromised web pages to go through.
While modern browsers are not immune to web vulnerabilities, they typically include built-in mechanisms to filter-out known malicious websites. These mechanisms are usually based either on the properties of the page (e.g., no SSL certificates), or lists of known risky websites.
However, LayerX’s research has found that even these capabilities were – for the most part – not implemented in Comet and Genspark, leaving their users with increased vulnerability to phishing and web attacks.
LayerX tested three new AI browsers – Comet, Genspark, and Dia – and compared them against the two most popular non-AI browsers – Google Chrome and Microsoft Edge.
The LayerX research team tested each browser against the 100 most recent phishing attacks reported on leading vulnerability websites such as OpenPhish and PhishTank, and checked whether they were allowed to go through. We also compared them against LayerX’s own protections, deployed via LayerX’s browser add-on.
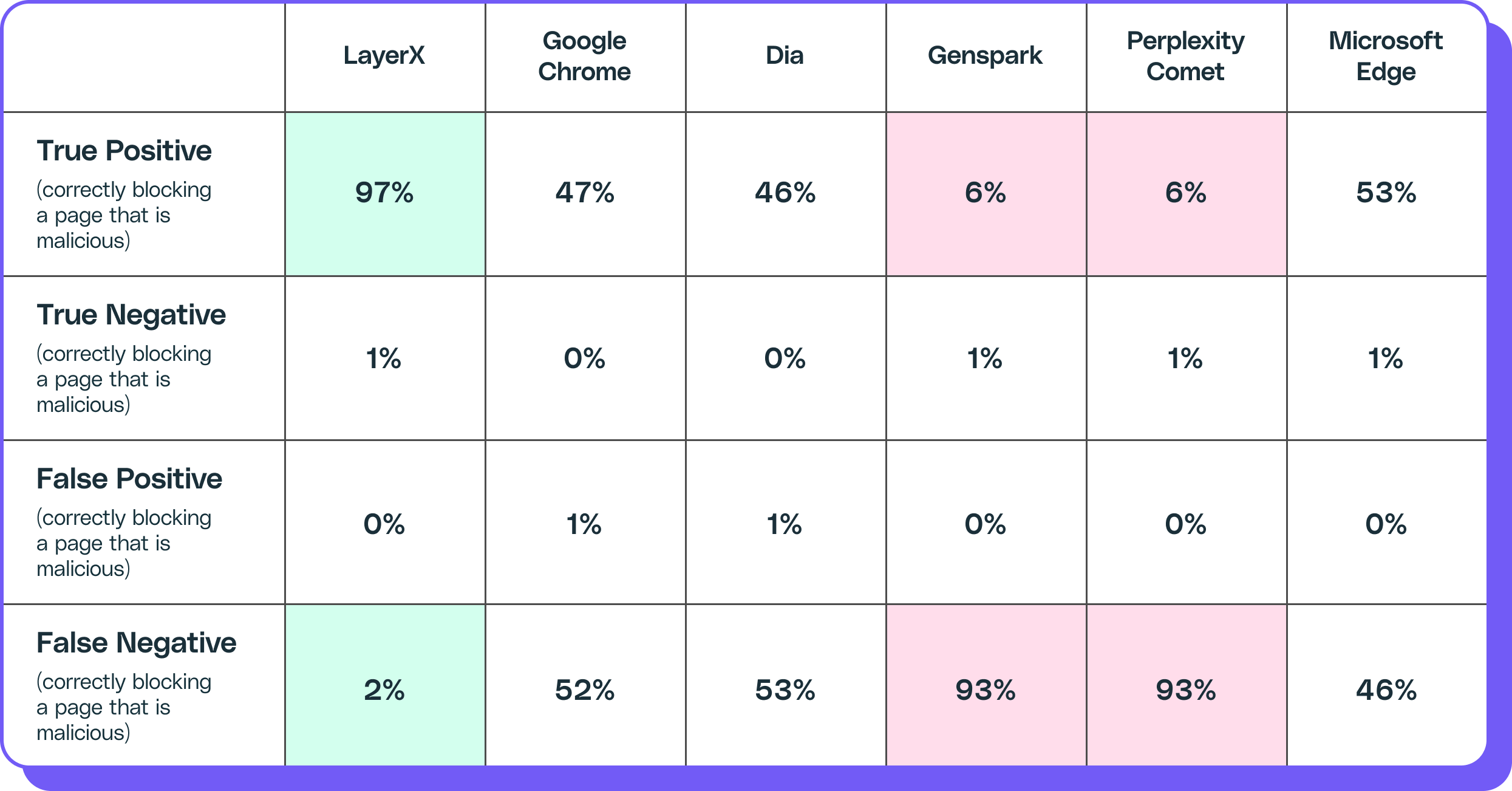
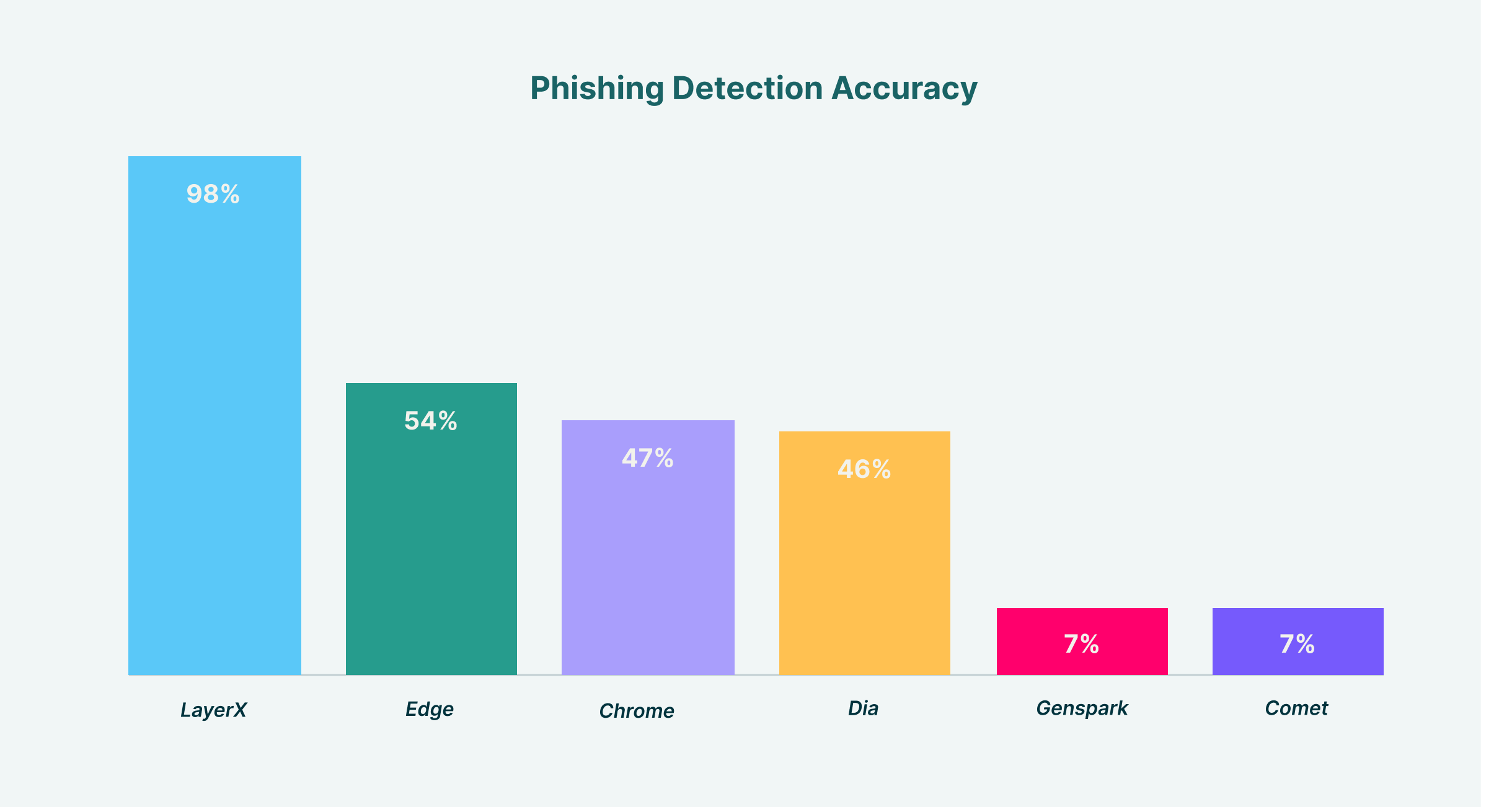
The findings show that Edge was the most effective browser at stopping phishing and web attacks out-of-the-box, with a 54% success rate. Google Chrome came in second, with 47%, followed closely by Dia, at 46%. Closing the pack were Comet and Genspark, at only 7% each.
However, LayerX’s built-in AI protections achieve a 98% accuracy rate in detecting phishing attempts, showing how external protections, such as those offered by LayerX, can effectively protect browser users from phishing.
Most Browsers Use Google for Underlying Code – and Phishing Protections
To understand how most browser phishing protections work, we first need to understand web browsers.
Chrome is far-and-away the most popular browser today, with over 70% global market share.
However, Google makes Chrome’s foundational source code (minus some proprietary elements and add-ons) open under the Chromium Project. As a result, most web browsers today, including Microsoft Edge, Arc, Brave, Opera, and others, are derivatives of Chromium. This means that under the hood, most web browsers today work similarly, with differences coming mostly in the user interface and extra features.
As new AI browsers begin to emerge, they, too, are mostly based on Google’s underlying foundation: Comet (by Perplexity), Dia (by The Browser Company), and Genspark are all based on Chromium.
However, apart from the browser source code, Google also provides built-in web security features to protect against risky websites.
Google provides the Safe Browsing service of lists of known bad URLs. These lists are available via the Safe Browsing API (for non-commercial use) or the Web Risk API (for commercial uses).
Google offers two layers of built-in phishing and vulnerability protections:
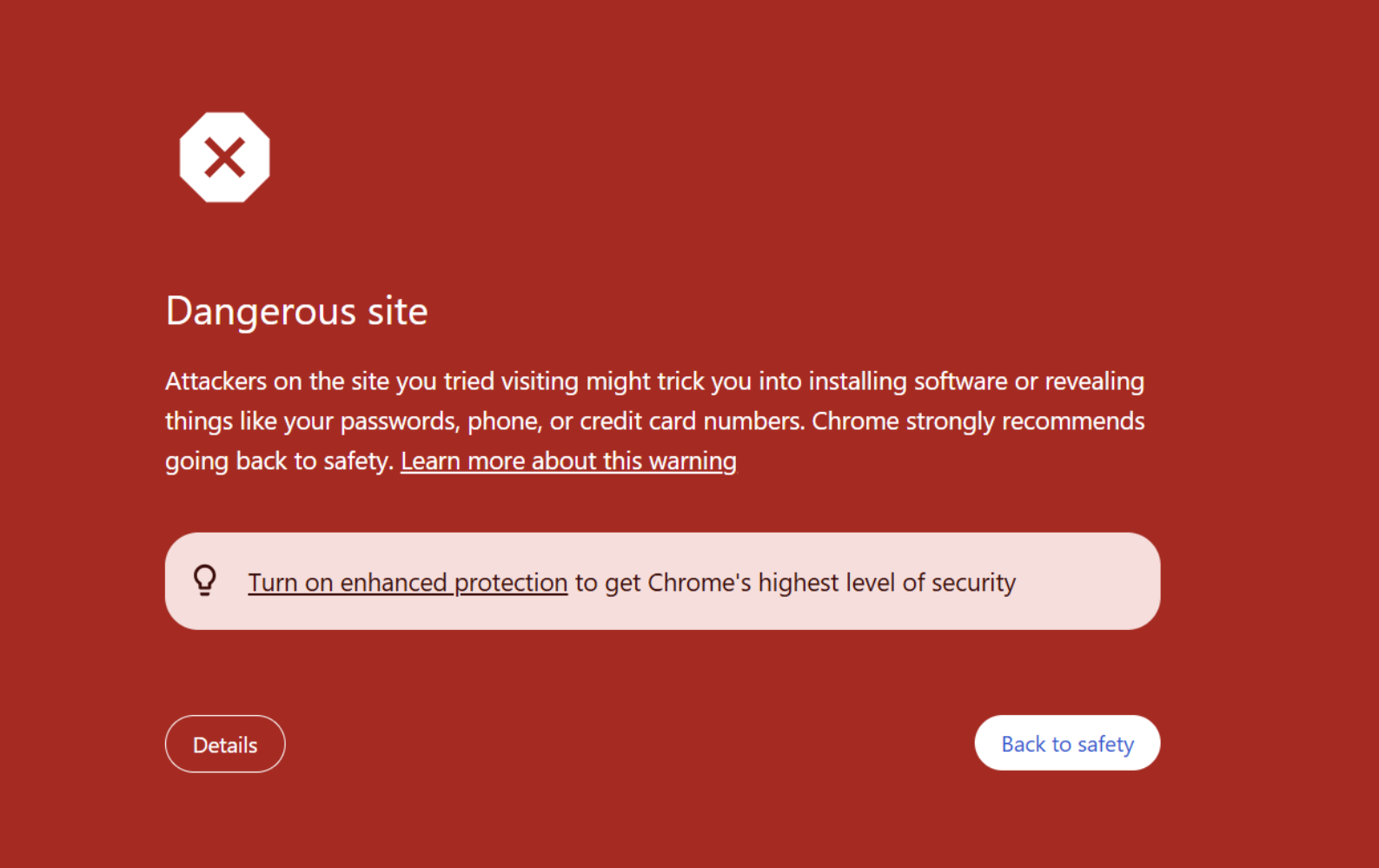
- Lists of Bad Known URLs: Protection against known existing malicious URLs, based on lists of previously-reported web pages. While this covers only already known bad URLs, and does not protect against 0-hour and rapidly-rotating URLs, it provides reasonable protection against known bad websites. This protection is seen in blocking pages with a red background (the “red block” pages).
- Detection of Insecure Connections at the Network Level: Protection against pages with faulty, incomplete, or missing TLS/SSL certificates. While errors with encryption certificates are not, of themselves, evidence of malicious activity, they are often indicators of fake or masquerading pages. These errors are seen in blocking pages with a white background (the “white block” pages).
We found that most browsers in this test – all of whom are Chromium derivatives – used Google’s underlying protection to some degree. However, LayerX found significant variances in the extent of usage and breadth of protection.
Edge Had Best Overall Performance, Comet and Genspark Lag Far Behind
Analyzing performance across all browsers showed that Edge had the best overall built-in phishing protection, with a 54% accuracy rate. Edge was the only browser that seems not to be using Google’s phishing protections. While they were both overall similar in their assessment of about 80% of websites, we found that for about 14% of sites, Edge had an advantage, while Chrome was more accurate in identifying phishing incidents for about 6% of websites.
While Edge blocked only slightly more than half of unsafe websites tested, it provided the best out-of-the-box performance of all browsers tested, and surpassed Chrome. This means that Edge (and Edge Copilot Mode) users are the best-protected among users of commercial and AI browsers (without augmenting it with external phishing protections, of course).
Chrome – the industry benchmark – blocked fewer than half of malicious sites tested, at 47%. While Chrome’s built-in mechanisms demonstrated effectiveness in nearly half the case, this test demonstrates how the built-in mechanisms of the world’s most popular browser miss more than half of phishing instances, leaving users exposed.
Moreover, since Chrome’s safe browsing protections are based on lists of known bad URLs, by definition, they leave users vulnerable to new “zero-day” phishing attacks that have not yet been flagged and have not made it into lists of threat intelligence feeds of risky websites. In addition, since even small changes in the URL can render this identification meaningless, attackers are increasingly deploying phishing kits with rapidly rotating URLs with short “live” times, so that by the time the URL has been flagged, they have already moved to a new URL. That means that phishing protections requires a more dynamic approach that relies on scanning of page contents and context, and not just URL reputation.
Dia, which correctly identified 46% of phishing websites, was virtually tied with Chrome, indicating that they fully implement Google’s safe browsing APIs. Practically every single page that was blocked by Chrome was blocked by Dia, and vice versa. Conversely, pages that were not blocked on Chrome were also allowed through on Dia. Overall, the two browsers were in concurrence in 97% of cases. In both instances, blocking actions were primarily based on the URL being marked as an unsafe URL, via the “red block” pages.
What small variations (about 3% of cases) that we did identify in phishing protection of Dia compared to Chrome we attribute to minor time gaps between our tests and the bad URLs being updated in Google’s lists. Overall, our research indicates that Dia users have a level of security on par with that of Google Chrome.
Sadly, we couldn’t say the same about other AI browsers.
Comet and Genspark Showed Major Gaps in Protection
LayerX’s research shows that Comet and Genspark both displayed major gaps in protection against phishing attacks.
Analyzing 100 phishing websites, it appears that neither Comet nor Genspark implement Google’s safe browsing protections against known malicious pages. In both cases, they stopped only 7% of known phishing pages, and failed to block 93% of known active phishing sites.
To illustrate, below is a short video showing how well Comet, Genspark, Dia and Edge faired against a known malicious URL. Whereas Edge and Dia (based on Google lists) blocked it, Comet and Genspark allowed it to go through:
Nonetheless, not all is rosy across all browsers, and they all failed when facing an unknown “zero-day” phishing link:
LayerX, on the other hand, was able to correctly identify such attacks and block them with 98% accuracy:
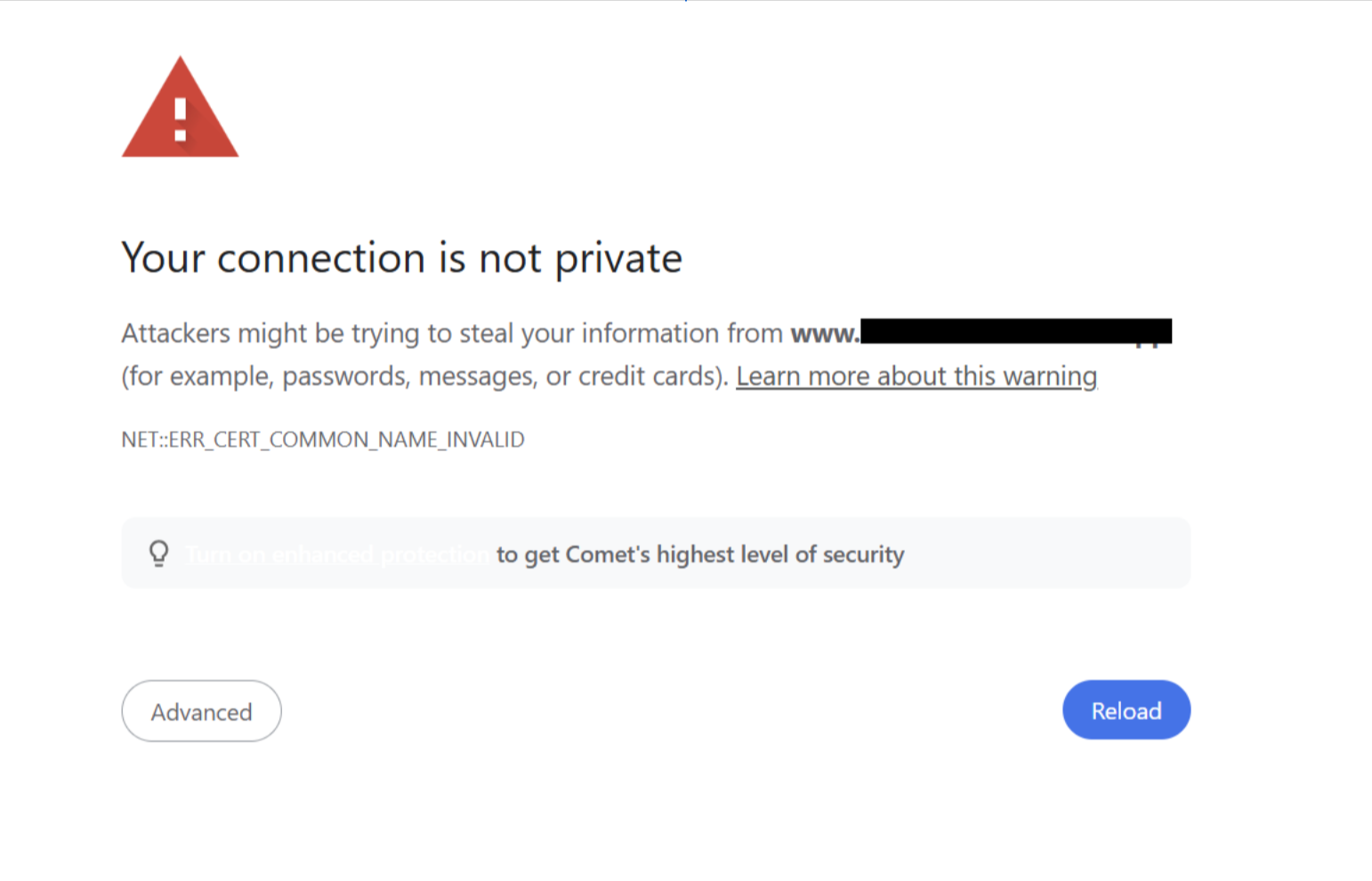
While known bad websites were being marked as such on Chrome and Dia (using the “red block” pages), no phishing page was blocked by Comet or Genspark in this way. This indicates that Comet and Genspark do not implement safe browsing protections by Google, and do not provide active identification of malicious websites.
What few phishing pages were blocked by Comet and Genspark were done using the Insecure Connection pages (the “white block” pages). These types of blocking activities are not based on active identification of phishing pages, but rather on identifying errors at the network level.
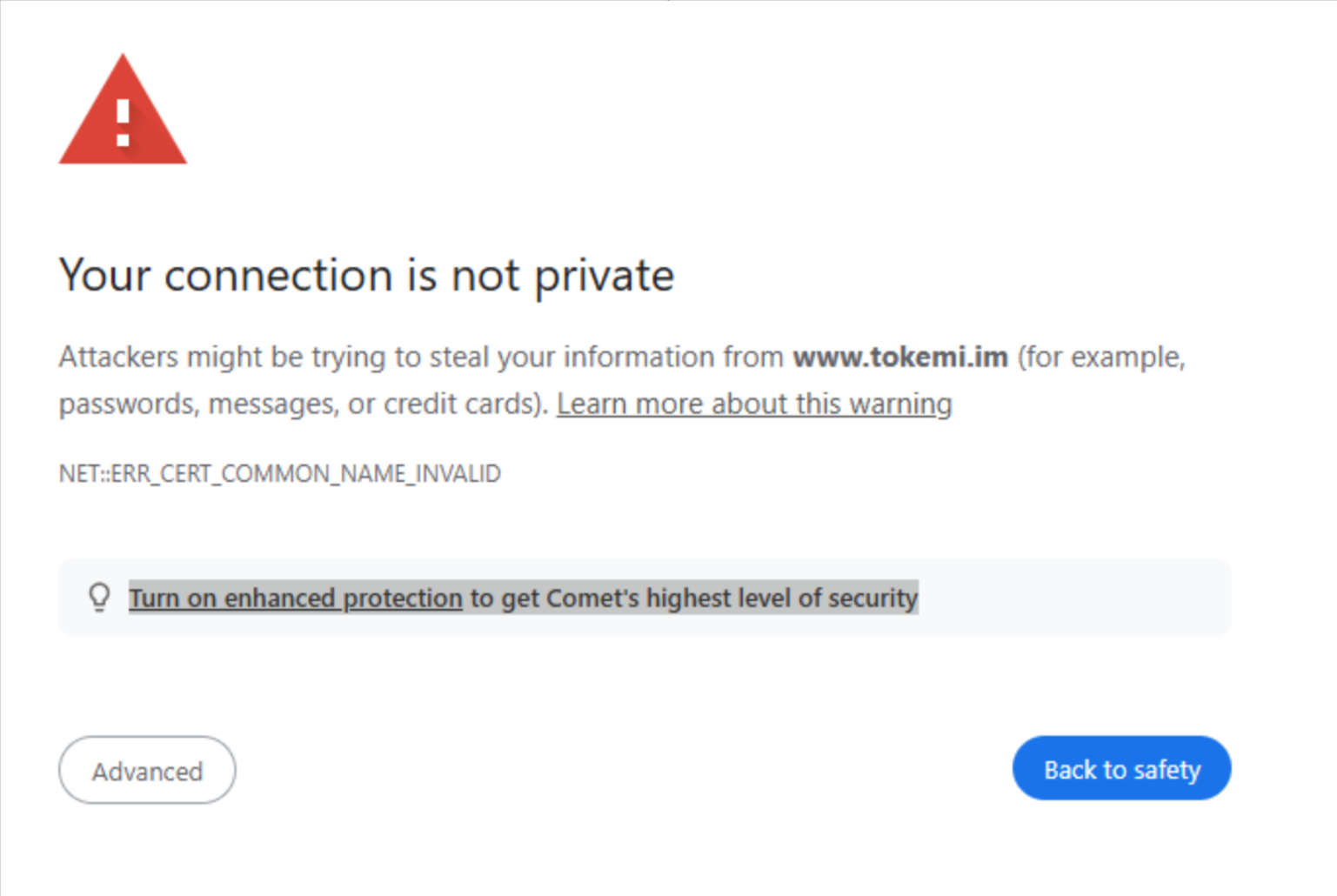
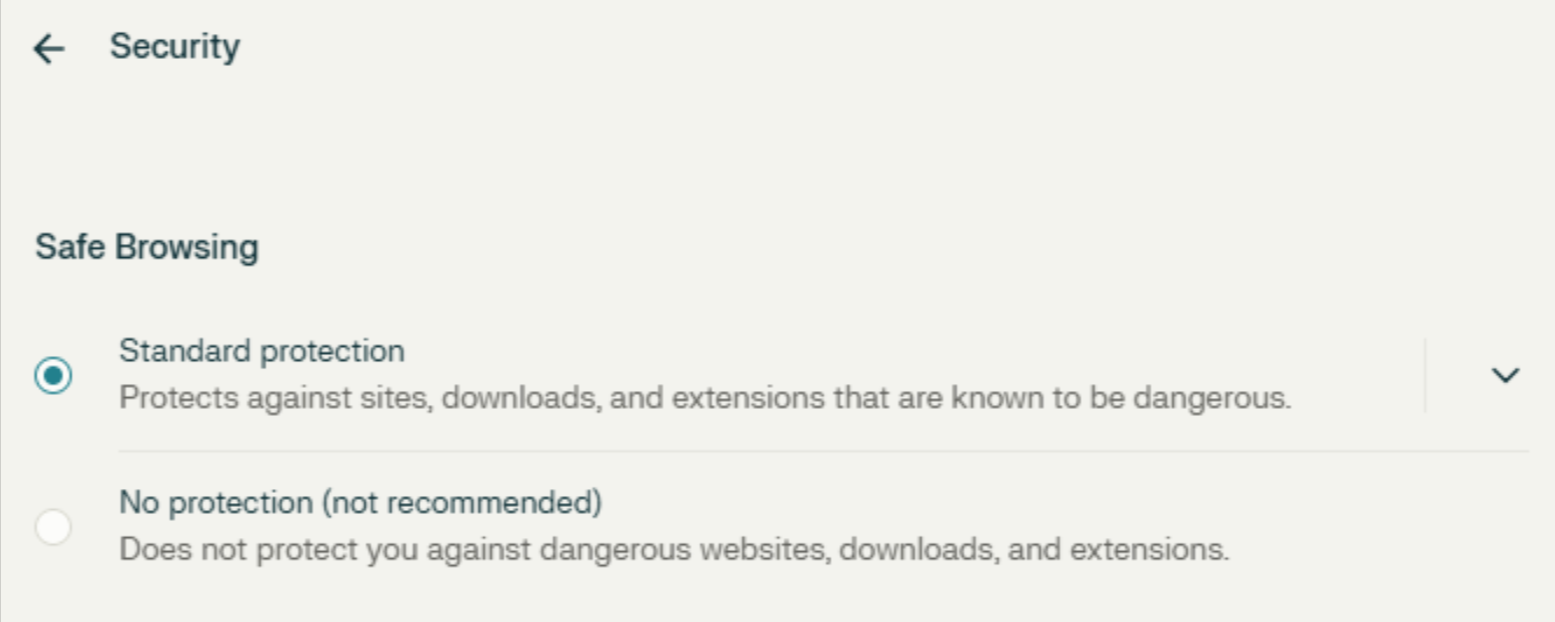
Interestingly, Comet’s blocking pages include a prompt to users to “Turn on enhanced protection to get Comet’s highest level of security” (seen highlighted below).
However, clicking those links led to a Security settings page where “Safe Browsing” Standard protection was already supposedly enabled, with no option for “Enhanced” security.
Based on our analysis, users of Comet and Genspark browsers are disproportionately exposed to phishing and malicious web pages, up to 85% more so than users of Chrome, Edge and Dia.
When the AI is In Your Browser, Phishing Protection is More Important Than Ever
The emergence of agentic AI browsers which can autonomously navigate websites, complete transactions, and access sensitive accounts on users’ behalf has created unprecedented security vulnerabilities that make robust phishing protections more critical than ever before.
Unlike traditional browsers where users manually interact with websites, agentic browsers operate with full user privileges across all authenticated sessions, including banking, healthcare, and email accounts. This creates a massive attack surface where a single compromised interaction can have catastrophic consequences.
As demonstrated by Brave’s research into Perplexity’s Comet browser, attackers can embed malicious instructions in seemingly innocuous web content, such as white text on white backgrounds, HTML comments, or even Reddit comments, that trick AI assistants into performing unauthorized actions.
These “indirect prompt injection” attacks bypass traditional web security mechanisms like same-origin policy and CORS protections because the AI operates as a trusted user agent. When an AI browser processes webpage content to summarize or interact with it, malicious instructions hidden within that content can redirect the AI to steal login credentials, access banking information, or exfiltrate sensitive data to attacker-controlled servers.
The vulnerability is particularly dangerous because attacks can occur through user-generated content on platforms the attacker doesn’t control, and execution happens automatically without additional user input once triggered. A simple request to “summarize this page” can result in complete account takeover or financial theft.
For these reasons, it is more critical than ever for AI browsers to implement new, specific protections against phishing attacks. This includes ensuring that the browser distinguishes between trusted and risky web content, identifying both known and unknown phishing attacks, and minimizing the risk surface for users of AI browsers.
Summary: It’s a Scary New AI Browser World Out There
The emergence of new, agentic AI browsers, while offering powerful new capabilities, also introduces significant security risks.
As LayerX’s research demonstrates, AI browsers like Perplexity’s Comet and Genspark show a drastic lack of built-in phishing protections, making them up to 85% more vulnerable than Chrome. This is particularly concerning given their ability to autonomously interact with web content and sensitive user accounts, opening the door for new attacks like indirect prompt injections and are in urgent need of additional layers of protection.
While browsers like Microsoft Edge and Google Chrome offer a degree of security against known threats, their protections are often insufficient against rapidly evolving, “zero-day” attacks. This highlights the critical need for AI browser developers to prioritize robust, dynamic security mechanisms to protect users from new forms of web-based attacks.
For users and enterprises that are adopting new AI browsers, these findings underscore the importance of exercising extreme caution with AI browsers and augmenting their protection with additional security measures.
For additional information on how LayerX can protect you against phishing attacks on any browser, schedule a demo today.