In the last few years, both attackers and defenders have increased their capabilities in the infinite cat-and-mouse game. Attackers have scaled their phishing operations for stealing credentials and identities. Defenders have adopted a zero trust security approach in which users often use their mobile devices to authenticate into their desktop applications. The chase goes on.
In a recent, quite fascinating, campaign, attackers have exploited this recent defender progress, leveraging a desktop attack surface in order to distribute a malicious mobile (iPhone) application.
Malicious iPhone applications are not easy to sneak into the app store. When successful, they can be used in various ways to conduct identity theft. Do you trust your employees’ mobile device to authenticate them into your SSO connected applications? Make sure they are protected.
TL;DR – Attack steps
- Distribution – Malvertising on a popular free streaming website.
- Fake video scam – Asking users to scan a QR code with their mobile device.
- Cross device hopping – The QR code opens a crafted social engineering landing page on the employee’s mobile device.
- Payload – The attack redirects the user to download a malicious mobile app from the app store.
Distribution
According to LayerX researches, the attack starts with a prominent malvertising campaign of a URL of a fake video. In this attack, the malvertising was distributed via a popular streaming website, hxxps://fmovies.to (ranked #715 worldwide!). It should be highlighted that the same malvertising infrastructure was seen pushed on other websites, many of which provide free streaming of movies, sports matches, and TV shows.
This is a good time to remind ourselves a basic truth about the web: if it is free then you are the product!
Fake video
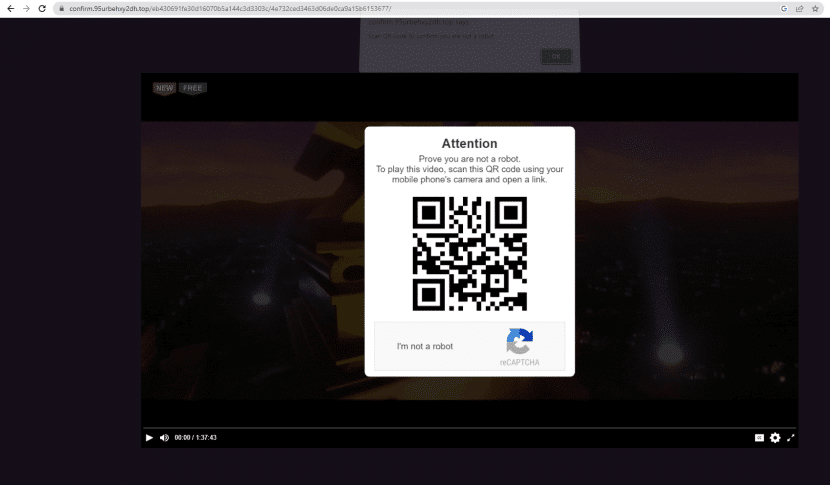
The malvertising payload is a URL of a fake video the user was hoping to watch.
Fake video payload of the malvertising campaign
Two seconds into the video, the screen is overlaid with a QR code and instructions to scan it using a mobile device. This page (as well as several other instances) was caught by the LayerX real-time threat prevention engine, which scans suspicious web pages from within the browser.
It is worth mentioning that the same infrastructure distributes different landing pages each time. Therefore, we estimate it is an independent venture that is monetizing on landing pages delivery. We also believe its owner is not the same one as of the next step of the attack.
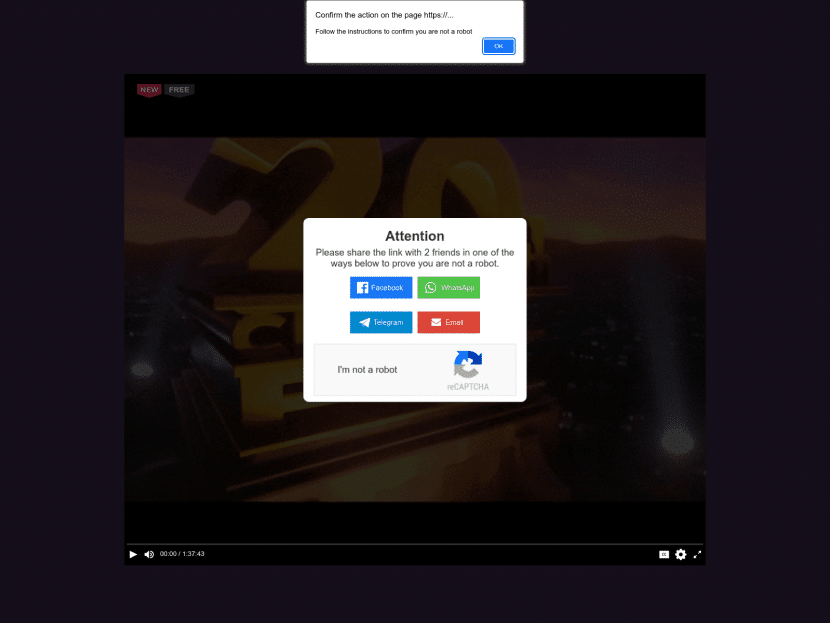
Here’s another example of a different prompt initiated by the fake video:
hxxps://watch-online.7vuoh5i80tys.top/share/5/
Needless to say, scanning the QR code doesn’t give access to the movie, but leads to the next step of the attack, performed on the mobile device. However, don’t throw away your popcorn, as this social engineering attack will soon display great acting and special effects…
Mobile device social engineering
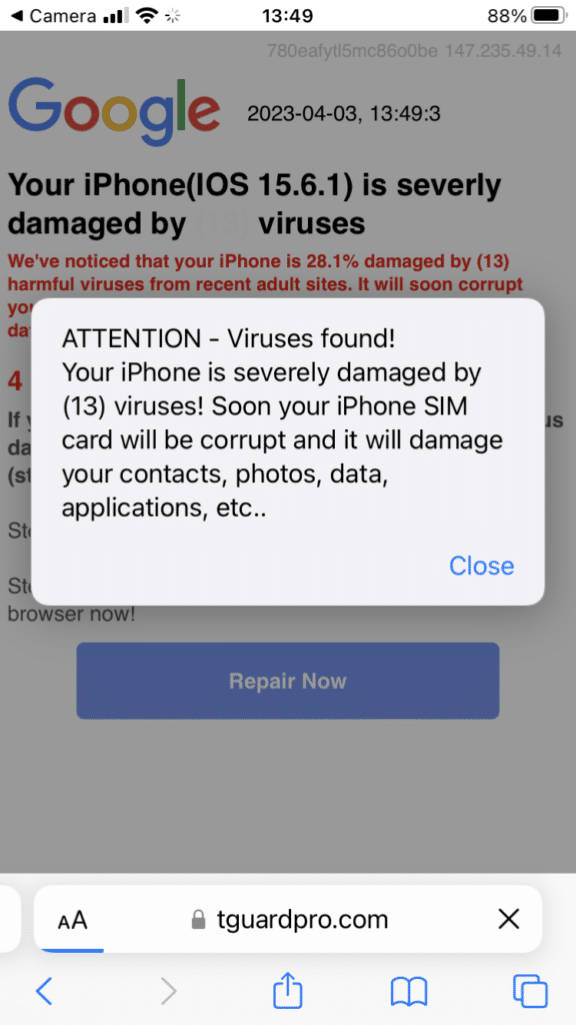
LayerX’s threat research team has researched this attack and accessed it from an iPhone mobile device. The QR code opens a malicious landing page with a fake security prompt.
Fake iPhone security prompt
The prompt shows scary warnings of viruses found on the device that will soon corrupt the device SIM card!
The URL shows that the landing page is leveraging the device metadata it has access to and building a tailor-made landing page. There is nothing special about the content except for it being used for social engineering; all device attributes are accessible to mobile landing pages.
This cross-device hopping is a great technique used by attackers to trick standard security systems. Once a user scans a malicious QR code, the organization can lose visibility into the affected mobile device.
Since us LayerXers expected to see a movie, we had no choice but to click the “repair now” button and see what happens next.
Payload
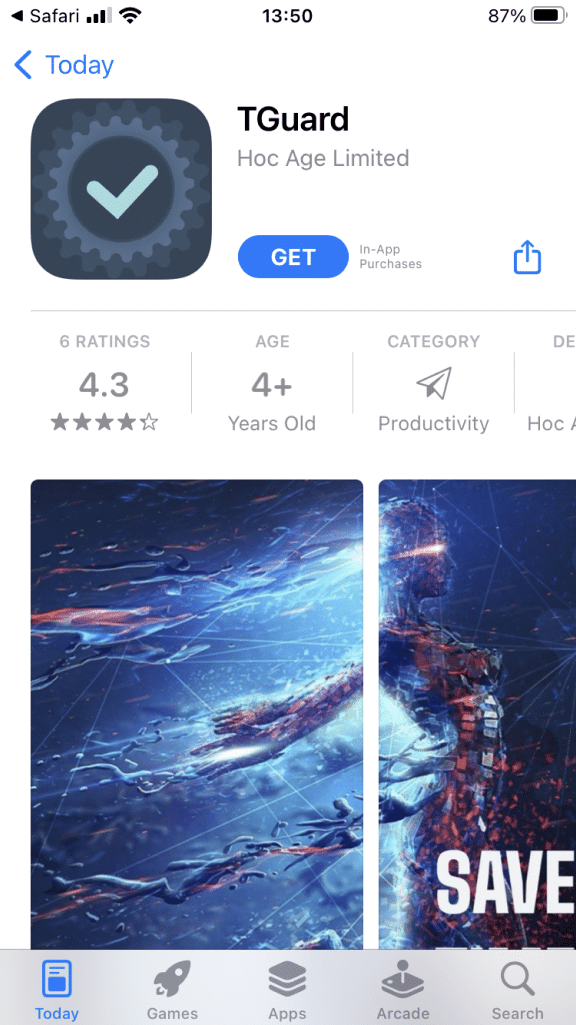
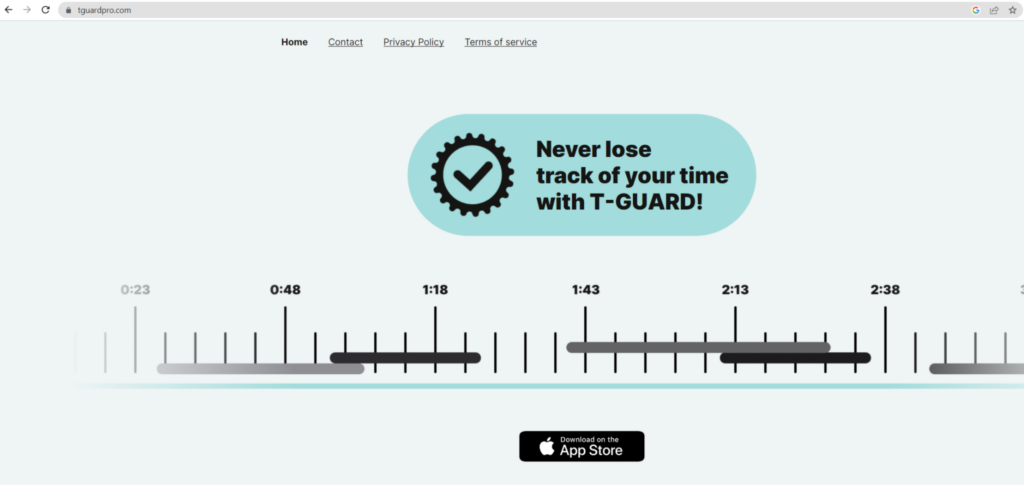
TGuard application
The link led us to this mobile app page showcasing TGuard, which has since been removed from the app store. The app claims to provide productivity functionalities (such as time tracking) and may well have targeted both enterprise users and regular users.
Although the mobile app has been removed, the operators’ website is still in the air:
Summary
This creative campaign is an outstanding example of how attackers easily infiltrate the corporate perimeter by leveraging the human element. It is the same human weakness that causes us to see free streaming sites as a righteous, philanthropist venture, scan a shady QR and then install a mobile application from an unknown source.
The functional innovation of this attack is the cross-device hopping. I think that only a handful enterprises today are capable of detecting such an attack that targets the employees’ unmanaged mobile devices.
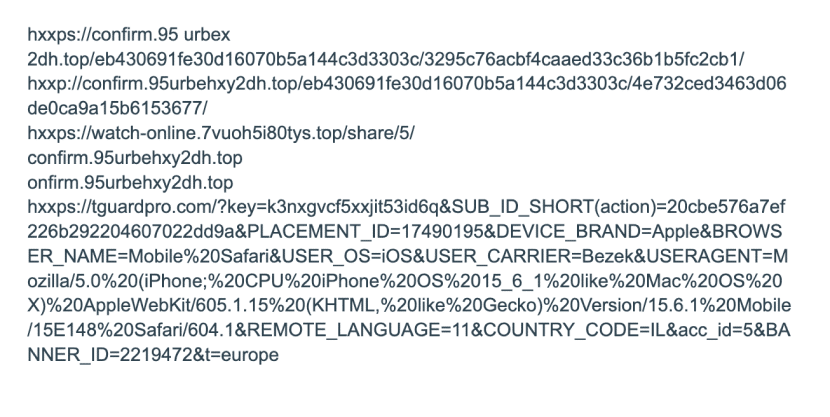
IOCs: