In a tech world obsessed with growth, innovation, and speed, few stories hit as hard as the unfolding battle between two of the industry’s most prominent competitors: Rippling and Deel.
Both are high-flying HR tech unicorns, shaping the future of global workforce management and payroll. But beneath their polished pitches and billion-dollar valuations, a darker narrative has emerged—one involving a corporate mole, stolen customer data, manipulated deals, and a lawsuit that could redefine how we think about data security in the age of remote work and real-time collaboration.
But this isn’t just a one-off headline-grabbing scandal. It’s a wake-up call.
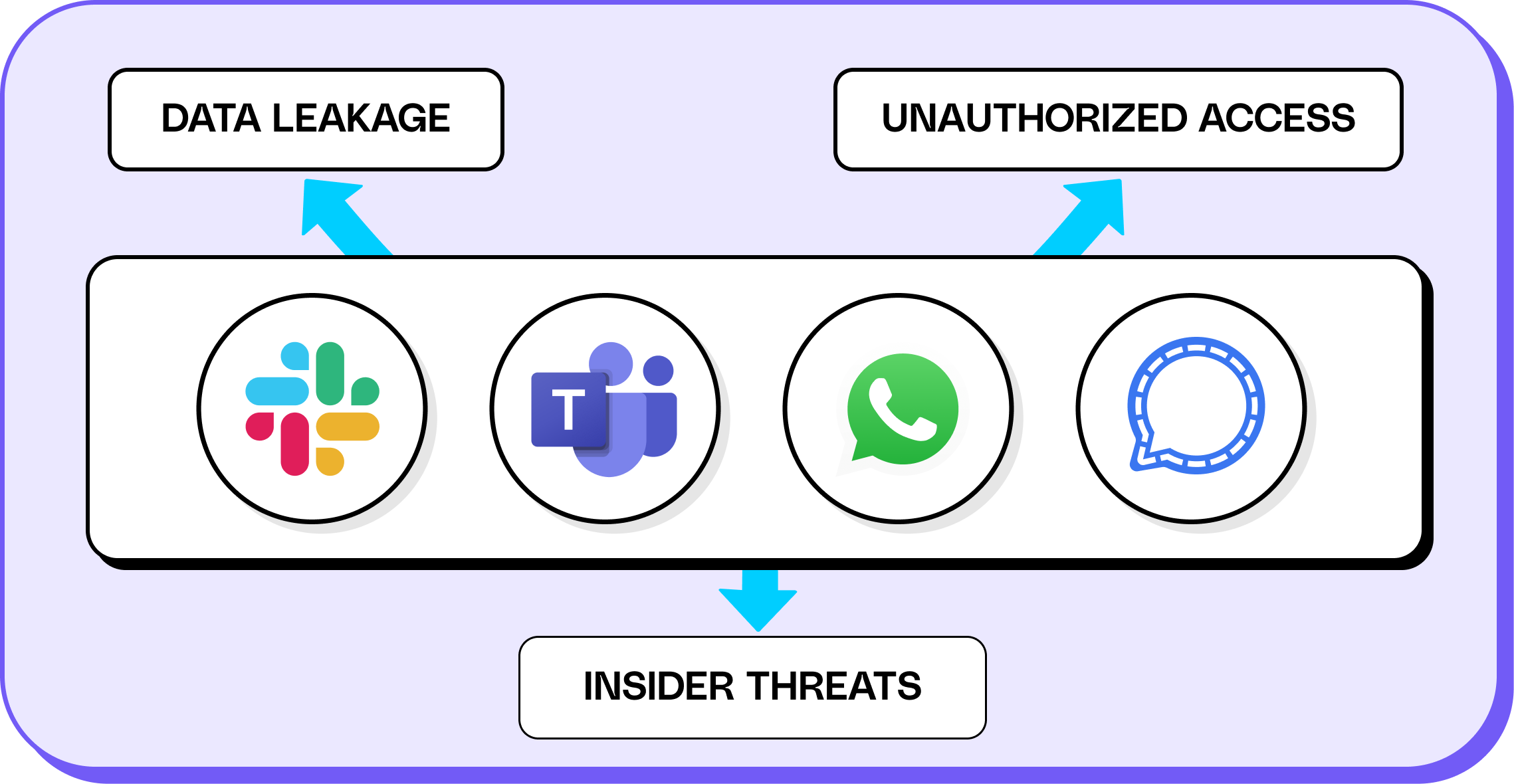
This case shines a spotlight on a broader, more urgent issue: the security blind spots created by modern communication platforms like Slack, Microsoft Teams, and WhatsApp. As companies race to stay agile and connected, they’re unintentionally opening up vast new surfaces for insider threats, data leakage, and unauthorized access.
In this blog, we’ll unpack what happened in the Rippling–Deel espionage case, explore how messaging tools have become both indispensable and dangerous, and outline what every modern organization must do to protect its data in this new threat landscape.
Inside Silicon Valley’s Most Explosive Corporate Espionage Scandal
Rippling and Deel are among the fast-growing tech unicorns operating in the global HR, payroll, and workforce management space. As these two giants clashed for market share and enterprise clients, tensions escalated into one of the most shocking revelations in recent tech history: a case of corporate espionage involving a planted mole.
The story reads like a tech thriller:
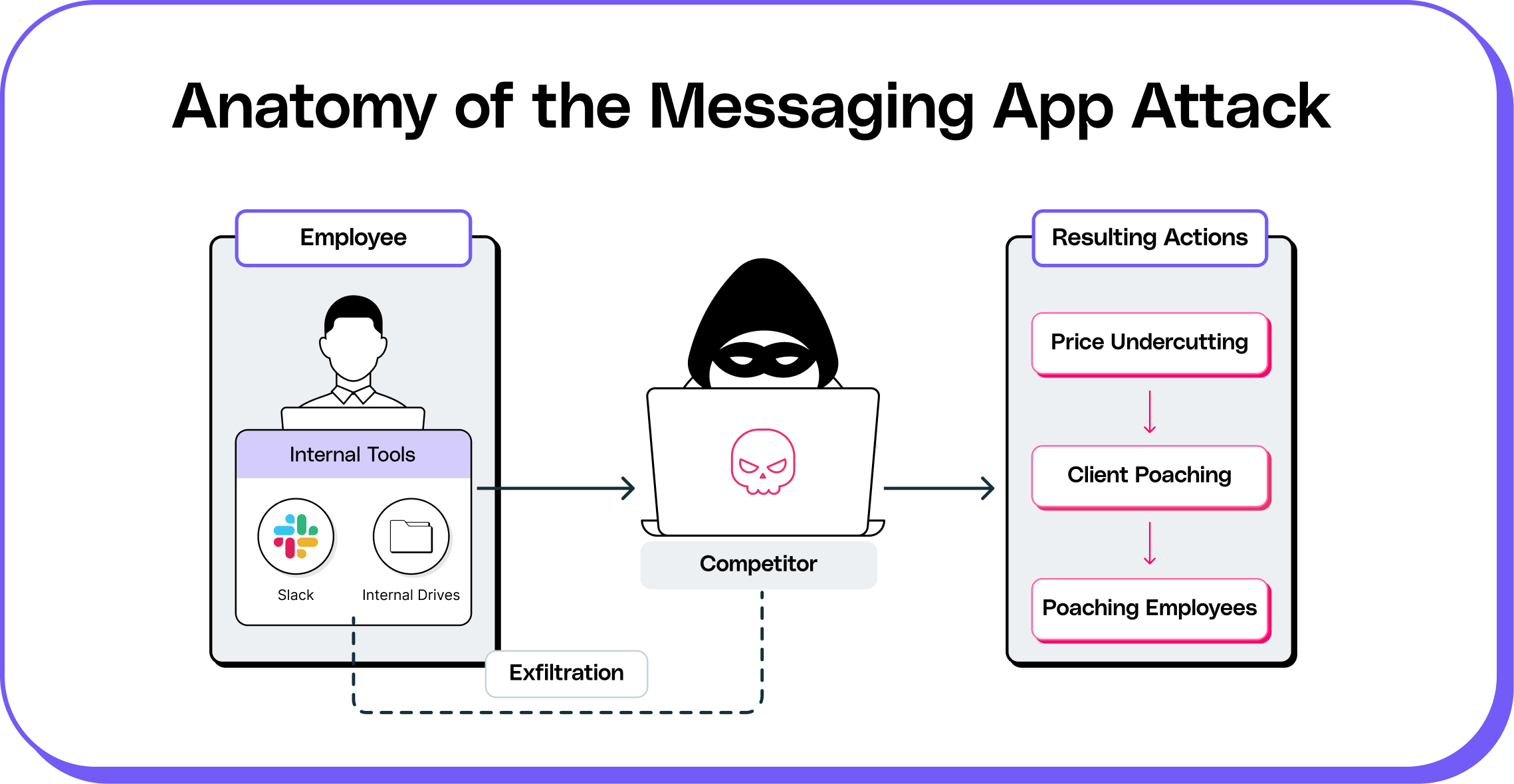
Rippling uncovered that one of its own employees was secretly working for Deel. Over several months, this mole accessed confidential channels including Slack, internal drives, and Salesforce, harvesting sensitive deal information and sales leads. He was feeding this intel to Deel, which used it to undercut pricing, intercept client deals, and even poach Rippling employees using internal HR data.
The clues started piling up when Rippling noticed eerily timed moves by Deel: product launches, client targeting, and pricing strategies that mirrored Rippling’s internal plans a little too closely. Sensing something was off, Rippling set a trap—a decoy Slack channel designed to lure the mole in. It worked. The spy was exposed, and Rippling filed a lawsuit demanding over $100 million in damages.
But this isn’t just a story about two tech companies in conflict—it exposed a deeper, industry-agnostic vulnerability of how reliant modern workplaces have become on instant messaging platforms like Slack, Microsoft Teams, WhatsApp, and others. While these tools are the digital hallways of the modern office, they’re also rapidly becoming the front lines of corporate cybersecurity and insider threats.
The Rise of Instant Messaging Tools in the Workplace
Slack, Teams, WhatsApp, Signal, and even Discord have evolved from casual communication tools to mission-critical enterprise infrastructure. Employees use them not just to chat but to share strategy documents, product roadmaps, code snippets, customer data, and legal agreements—often more freely than in email.
Their adoption has skyrocketed thanks to remote and hybrid work, with organizations now juggling multiple platforms across regions, teams, and vendors. What was once a support tool has become the core collaboration layer of modern business.
But with speed and convenience comes risk.
The New Threat Landscape: Why Messaging Tools Are Hard to Secure
Messaging platforms introduce a new wave of security challenges that traditional tools simply weren’t built to handle.
1. Too Many Apps, Not Enough Oversight
Most organizations don’t just use one platform—they use several. Slack for internal discussions, Teams for meetings, Signal or WhatsApp for quick mobile chats. This creates a fragmented communication stack where IT and security teams have little or no visibility. Who’s talking to whom? What data is being shared? Across which accounts? The answers are often unclear.
2. No Files, Just Intelligence
Insider threats today aren’t exfiltrating files—they’re extracting context and intelligence from inline messages, pasted screenshots, and ephemeral messages. Because messaging data often isn’t stored as traditional files, legacy DLP tools and endpoint security solutions fall short, unable to detect what’s being shared or when sensitive information is leaking in real-time.
3. Informal Tone Breeds Oversharing
Chat feels informal. That’s why employees are far more likely to overshare without thinking, dropping internal launch plans, customer data, or even HR conversations into a group thread. This environment is ripe for insider threats or unintentional leaks, especially when no one’s watching.
4. Shadow Identities and Untracked Access
Many messaging platforms are riddled with accounts that fall outside corporate identity systems—contractors, partners, personal emails, or guest users. These unmanaged identities often bypass IAM controls entirely, making it almost impossible for security teams to know who has access, where they’re logging in from, and what they’re doing inside the system. This lack of visibility increases the risk of credential compromise, shadow access, data leakage and unmonitored insider activity.
What Organizations Must Do Now: Securing Instant Messaging Before It’s Too Late
If a tech-savvy, security-conscious company like Rippling can be infiltrated through something as routine as Slack, any organization is at risk. It’s time for security teams to evolve their playbook and re-evaluate how they secure their instant messaging platforms. Here’s how to get ahead of the threat:
1. Centralize Visibility Across All User Activity
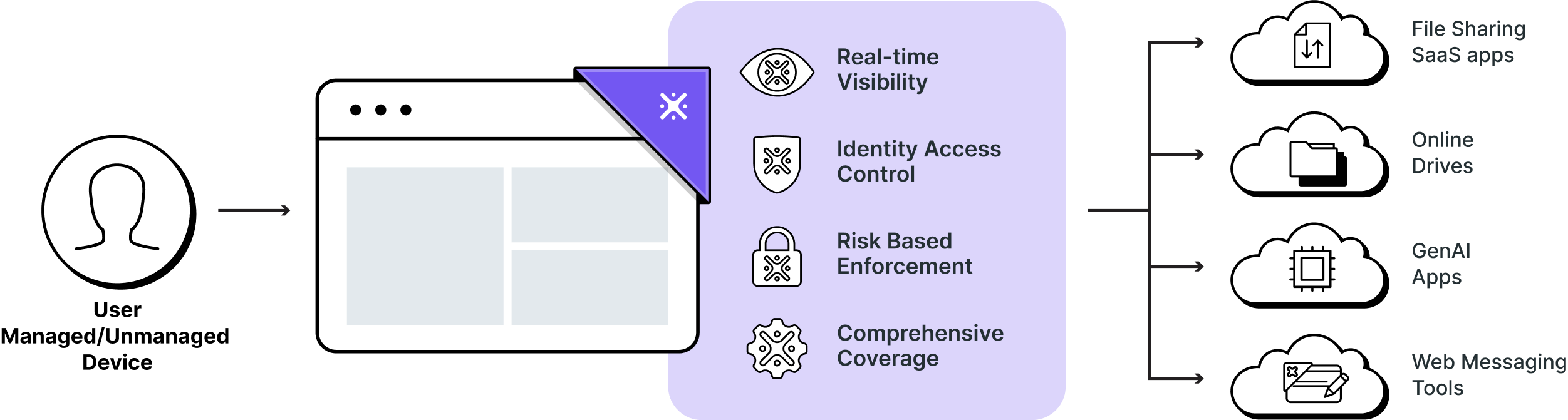
Most data leaks happen in the browser, but traditional tools can’t see what’s going on at the session level. Organizations must implement a browser-based security solution that provides full visibility into user behavior across Slack, Teams, and other SaaS apps that include logins, file uploads/downloads, copy-paste actions, data input, etc.
2. Deploy Context-Aware DLP Tools
Modern collaboration isn’t built on attachments anymore. It’s inline text, code snippets, screenshots, and links. Deploy context-aware DLP solutions that can interpret and classify sensitive data even when it’s embedded inside a chat or pasted into a message, not just when it’s sent as a file.
3. Run Insider Threat Simulations
Don’t wait to be blindsided. Proactively test your organization’s ability to detect suspicious behavior—just as Rippling did with its honeypot Slack channel. These tests can reveal blind spots before a real breach occurs.
4. Train Employees for the Messaging Era
Security awareness must go beyond phishing and password hygiene. Teams need to understand the risks of oversharing in chat, how to spot suspicious behavior, and when to report unusual messages, even if they seem minor.
5. Deploy Last-Mile Browser Controls
Most of the non-file data activity takes place within the browser, in SaaS applications such as Office365, Google Workspace, Salesforce, webmail and web-based messaging applications. This makes the browser the main point of risk for data leakage, and the point of control that organizations must secure.
How LayerX Helps Secure the Modern Workspace
All of these challenges—from insider threats to fragmented messaging tools—point to one clear need: deep visibility and control over what users are doing in the browser, where most collaboration now happens.
That’s exactly where LayerX comes in.
LayerX is an all-in-one, agentless browser security platform built for the way work actually happens today—inside web apps, across multiple messaging platforms, and on both managed and unmanaged devices.
With LayerX, organizations gain:
- Complete visibility into all user identities and activity across Slack, Teams, WhatsApp, and other SaaS tools—from logins and file uploads to message content and data transfers
- Real-time monitoring and control across all browsers and devices, without the need to install heavy agents or change user behavior
- Adaptive, risk-based protections that automatically block unauthorized sharing of sensitive data before it leaves the organization
Whether you’re defending against accidental leaks or deliberate espionage, LayerX equips your team with the tools to stay one step ahead.
Contact LayerX for a personal demo to showcase how we can help you secure your IM and browser-based SaaS applications and prevent the next data breach.