Let’s be honest, when most people think of a “cyberattack,” they picture hoodie-clad hackers hammering away at firewalls from some dark basement. But reality? It’s much less cinematic and a lot more dangerous.
The truth is, sometimes the threat is already logged in.

That’s what makes insider threats so devastating. They don’t break down doors but walk right through them. Just like what happened with Coinbase.
The Coinbase Breach: When Insider Access Turned Dangerous
In a startling revelation that has rocked the fintech and crypto industries, Coinbase, the largest cryptocurrency exchange in the U.S., became the target of a sophisticated case of corporate espionage. Unlike conventional cyberattacks that rely on technical exploits, this incident highlighted a more insidious vector: human vulnerability.
In Coinbase’s case, the breach didn’t originate from code or servers, but from its customer support channels—specifically, offshore contractors with access to internal SaaS tools. Instead of using traditional hacking methods, the attackers employed a more deceptive tactic by bribing overseas customer service contractors to gain access to Coinbase’s internal systems. These malicious insiders provided attackers with sensitive customer data, including names, addresses, phone numbers, email addresses, partial Social Security numbers, and images of government-issued IDs. Since they had unmonitored legitimate access to internal systems and SaaS tools, no one questioned a thing until the damage was already done. The attackers then used this data as leverage, demanding a $20 million ransom under threat of leaking or selling the information on the dark web.
This incident exposed sensitive information of nearly 97,000 users and underscored a sobering reality: insider threats remain one of the most dangerous and difficult challenges in cybersecurity today.
Access Without Visibility: The Modern Enterprise’s Silent Security Gap
In the era of cloud apps and remote work, the new security perimeter is not your network—it’s your people. The Coinbase breach highlights a growing trend in cybersecurity: the rise of insider threats, particularly among third-party contractors and support staff.
As perimeter defenses like firewalls and intrusion detection systems have become more robust, attackers are shifting their focus to individuals inside the organization who already have access. These insiders don’t need to “hack” into systems—they’re already inside the walls. Whether driven by greed, coercion, ideology, or desperation, insider threats are far more difficult to detect and stop using traditional security measures.
Third Parties: They’re In Your Systems But Off Your Radar
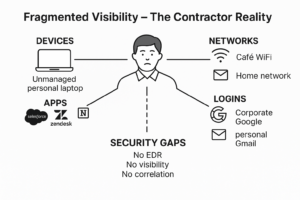
The modern enterprise runs on contractors, freelancers, outsourced support teams, and third-party vendors. These workers often need access to the same tools your full-time staff uses—SaaS platforms like Salesforce, Zendesk, Notion, Google Workspace, and more. Most SaaS platforms, while feature-rich, lack native security controls to detect or block risky behavior once a user is logged in. Once a contractor gains access, traditional perimeter defenses become irrelevant. There’s no firewall between a browser tab and a database export.
Unlike your internal teams that are onboarded through secure IT processes, third-party users often operate on:
- Unmanaged personal devices – Contractors often use their own laptops or mobile devices that aren’t controlled or secured by the organization’s IT team, leaving them vulnerable to malware or data leaks.
- Unsecured home or public networks – Working from cafés, airports, or home Wi-Fi networks without proper encryption exposes sensitive company data to interception and unauthorized access.
- Shadow Identities and Untracked Access – Many third-party users are granted more permissions than necessary and often bypass IAM controls entirely, making it almost impossible for security teams to know who has access, where they’re logging in from, and what they’re doing inside the system. This lack of visibility increases the risk of data leakage and unmonitored insider activity.
- No behavior monitoring and visibility – Without real-time tracking of user actions inside SaaS apps or web platforms, organizations are blind to risky behavior until after the damage is done.
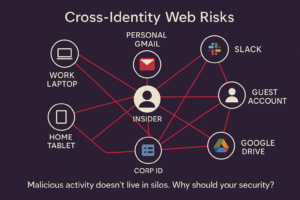
- Fragmented cross-identity activity with no correlation – Users operate across corporate and non-corporate logins, platforms, and devices, making it nearly impossible for traditional security tools to correlate fragmented data and detect malicious behavior.
And that’s the core issue: they’re inside your systems, but outside your security perimeter.
How Organizations Can Protect Themselves from Data Leakage by Malicious Insiders
As companies rely more on third-party teams and contractors, the browser becomes the weakest—and least monitored—link in the security chain. The Coinbase breach serves as a powerful reminder that no organization is immune to insider threats. With attackers becoming more sophisticated in targeting internal personnel, it’s imperative for companies to adopt proactive, behavior-based security measures such as:
- Limit Access with Least Privilege: Only give users access to the systems, data, and tools they absolutely need to do their jobs and nothing more. Especially for contractors and third parties, avoid broad or persistent access.
- Gain Real-Time Visibility Into User Behavior: You can’t stop what you can’t see. Organizations need tools that monitor what users are actually doing inside SaaS apps, browsers, and cloud environments.
- Detect and Block Risky Actions Instantly: Set up intelligent systems that detect risky behavior (e.g., mass downloads, file uploads to personal drives, suspicious logins) and can automatically respond in real time.
- Monitor Third-Party and Contractor Activity: Third-party users should never be treated like internal employees. Monitor their activity closely, especially when they’re accessing sensitive systems or customer data.
- Correlate Cross-Identity Activity: Don’t just monitor one account at a time. Malicious insiders often operate across multiple logins or devices. Link actions across different logins, devices, and apps to detect patterns and prevent users from hiding behind multiple identities.
Enter LayerX: The Watchtower for SaaS, Contractors, and Shadow Users
So, how do you stop this madness?
You could try installing agents on every contractor’s laptop or force everyone onto a corporate VPN until they revolt or find a workaround. Or better yet, you could meet users where the work happens: inside the browser.
LayerX operates where insider threats do their damage: the browser.
Unlike traditional tools that protect infrastructure or endpoints, LayerX is like strapping a high-resolution, always-on security camera to every browser session, without needing to install anything on the user’s device. It watches what users actually do inside SaaS apps, across identities, devices, and sessions and blocks all malicious activities in real-time.
Here’s how LayerX makes the invisible… visible:
- Browser-Level Visibility
LayerX monitors all user actions in real time across every browser, on any device, for every SaaS app—downloads, uploads, copy-paste, screenshots, and file-less transfers—right where data is handled. - Instant Risk Detection & Blocking
Suspicious behavior is automatically detected and blocked before data can be leaked without any manual intervention. - Cross-Identity Insight
LayerX connects user activity across logins, devices, and apps to uncover hidden patterns and prevent identity masking. - Context-Aware Decisions, Not Dumb Rules
LayerX doesn’t just follow rigid policies. It understands context: who the user is, where they’re working from, what device they’re using, and whether they are using corporate or non-corporate accounts. That’s how it knows when something’s off. - Seamless Deployment
LayerX runs directly as an extension in the browser and works across all devices and environments, including unmanaged ones. There are no agents, proxies, or disruptions.
With LayerX, you can scale confidently, collaborate globally, and protect your data no matter who’s on the other end of the screen. Whether it’s a careless employee or a bribed contractor, LayerX ensures your sensitive data never walks out the front door undetected.
Contact LayerX for a personal demo to show how we can help you secure your contractor and 3rd party threats, without breaking your existing flows or disrupting business continuity.