VDI (Virtual Desktop Infrastructure) is a technology that enables organizations to provide desktop environments to end-users from a centralized server or data center so they can access them remotely. In a traditional desktop environment, each user has their own physical computer with an operating system, applications, and data stored locally. However, with VDI, these resources are virtualized and hosted on a server, allowing users to access their desktops from a separate physical location.
There are two types of VDI deployments: non-persistent VDI and persistent VDI. Non-persistent VDI involves providing users with a standardized desktop image that resets to its original state after each session. This approach ensures consistency and reduces the management overhead, since any changes made by the user are discarded at logoff. Non-persistent VDIs are ideal for environments with high user turnover
Persistent VDI, on the other hand, offers each user a dedicated virtual machine with a personalized desktop experience. User modifications and data are retained across sessions, allowing for a more customized experience. Persistent VDI suits situations where users require personalized settings and the ability to retain data between sessions.
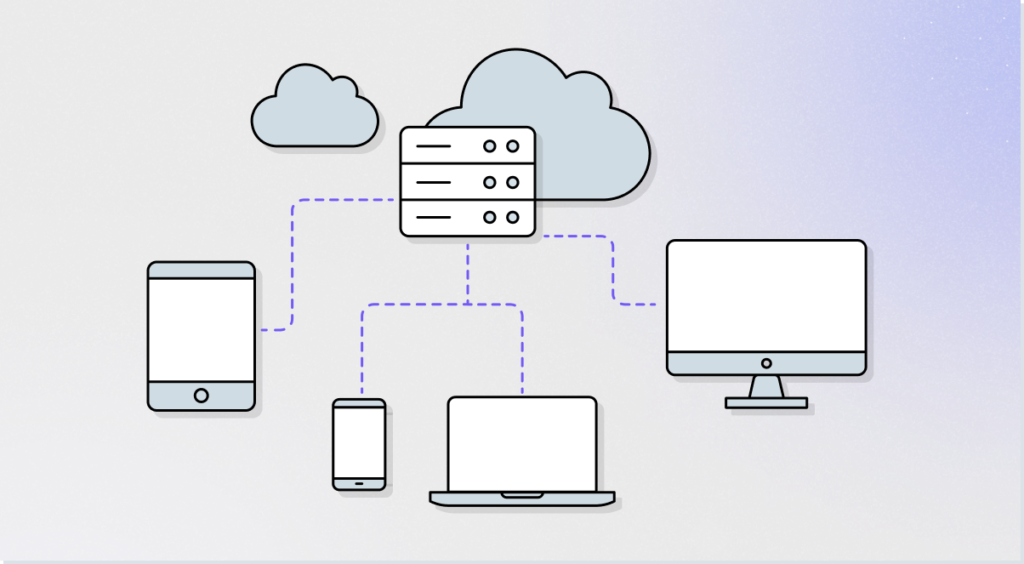
How Does Virtual Desktop Infrastructure (VDI) Work?
VDI solutions by separating the user’s desktop environment from their physical device and hosting it on a centralized server or data center. Here’s a high-level overview of how the VDI technology operates:
- Virtualization – VDI systems utilize virtualization technology to create and manage multiple virtual machines (VMs) on a server. Each VM represents a user’s desktop environment for them to access.
- Connection Broker: A connection broker acts as an intermediary between the user and the VMs and provides access. It receives requests from users, authenticates them, manages their connections, and assigns them to the appropriate VM based on their profile and resource availability. Users access their virtual desktops using client devices, web browsers, or client software installed on their physical devices.
- Desktop Delivery – The virtual desktops are delivered to the user’s device over the network. The user interacts with the desktop as if it were running locally, even though it is hosted and executed on a separate server.
- Data Management – User data and application settings can be stored either centrally on the server or on separate storage systems. This allows users to access their files and settings from any device while providing data security and control.
- Management and Maintenance – IT administrators can centrally manage and update the VMs, apply security policies, install applications, and monitor performance. They can also provision new VMs as needed and allocate resources based on user demands.
Risks of Virtual Desktop Infrastructure
While Virtual Desktop Infrastructure (VDI) offers advantages in terms of centralization, accessibility, and control, it also introduces certain cybersecurity risks that organizations must address. These include:
- Unauthorized User Access – VDI solutions provide remote access to desktop environments. An attacker can use the remote user credentials to gain unauthorized access to the network and to sensitive resources through the VDI access.
- Malware and Ransomware Attacks – If a virtual desktop is infected with malware or ransomware, it can potentially spread across the entire VDI infrastructure and the entire network, putting the organization at risk.
- Insider Threats – VDI environments can be susceptible to insider threats, where authorized users abuse their privileges to access sensitive data or introduce malware.
The Benefits of VDI
Virtual Desktop Infrastructure (VDI) offers several benefits for organizations:
1. Centralized Management
VDI allows for unified and efficient management of desktop environments. IT administrators can easily provision, update, patch and manage virtual desktops from a central server or data center. This centralized approach reduces the time and effort required for desktop maintenance and streamlines IT operations.
2. Device Flexibility and Mobility
VDI enables users to access their virtual desktops from various devices, including thin clients, laptops, tablets, or smartphones. This flexibility allows for remote work and a seamless transition between devices, providing users with the freedom to work from anywhere while maintaining a consistent desktop experience.
3. Scalability and Resource Optimization
VDI offers scalability, allowing organizations to easily add or remove virtual desktops based on demand. It also optimizes resource utilization by dynamically allocating computing resources to virtual desktops as needed, ensuring efficient use of hardware and reducing costs.
4. Cost Savings
VDI can result in cost savings over time. By centralizing desktop management, organizations can reduce hardware costs, extend the lifespan of devices, and lower energy consumption. VDI also simplifies software licensing and maintenance, potentially reducing software costs.
What is VDI Used For?
VDI (Virtual Desktop Infrastructure) is used for various purposes across different scenarios. Some common use cases of VDI include:
1. Remote and Mobile Work
VDI enables remote and mobile work by allowing users to access their virtual desktops from any device with an internet connection. This flexibility empowers employees to work from home, on the go, or from branch offices, while maintaining access to their desktop environment and business applications.
2. BYOD (Bring Your Own Device)
VDI facilitates the implementation of BYOD policies by separating the user’s desktop environment from the physical device. Employees can use their personal devices to access virtual desktops while keeping corporate data and applications within the centralized server or data center.
3. Workforce Flexibility
VDI supports flexible work arrangements, such as working in shifts, where employees can access their personalized desktop environments from shared workstations. This allows for better space utilization, cost savings, and increased collaboration.
4. Legacy Application Access
VDI enables access to legacy applications that may be incompatible with modern operating systems or hardware. By virtualizing the desktop environment, organizations can run legacy applications on a virtual machine with the required legacy infrastructure, ensuring continued access and functionality.
The Secure and User-Friendly Alternative to a VDI
VDIs enable remote access to users’ desktops. However, users are required to download the software, install it and cumbersomely connect to the VDI each time they want to connect to the system. IT are required to continuously patch and update VDIs, which is a time-consuming and meticulous task. And in the end, the VDI is not that secure either.
LayerX is a browser security solution, delivered as an extension, that is purpose-built to protect applications, data, and devices from all web-borne threats and risks. LayerX provides granular visibility into employees’ web activity and SaaS usage, across sanctioned and non-sanctioned apps alike. This radically simplifies management, maintenance and security overhead compared to VDIs.
LayerX also answers the security risks of VDIs:
- User Access – LayerX mitigates the risk of unauthorized access by using the browser as an authentication factor and enforcing consistent and granular authorization policies.
- Malware and Ransomware Protection – LayerX provides visibility into browser sessions at a granular level in a way that neutralizes malicious webpages and prevents malware injection.
- Insider Actions – LayerX enables visibility into user actions and enforces policies to prevent and alert about prohibited user actions, to minimize the risk of an employee maliciously exfiltrating data or injecting malware.