As organizations have shifted toward hybrid and global operations, the web is playing an ever-more critical role in how we communicate, research, and grow.
This ubiquity has resulted in a severe oversight: modern reliance on the web has vastly outpaced the security measures protecting browsing behavior. 88% of the 12.8 million websites currently infected by malware are not blacklisted by search engines, cybercriminals continue to hide behind legitimate safety measures such as HTTPS encryption, and a tenth of all malicious sites are actively disguised by non-malicious domains. At the intersection between internal device and global web sits the end-user, who all-too-often remains completely exposed or inadequately protected.
Older solutions attempting to address the gaping security void of the public internet have all relied on sacrificial security. Complex integrations spanning from web proxies to cloud-based isolation have added increasingly more weight to straining user experience and security teams.
Web security, which refers to protocols and protective measures that surround an organization’s operations, in order to protect employees and sensitive customer data, nullifies attacks without compromise. Web security is achieved when employees are supported with a single cohesive solution. Protection of the user’s experience and security – while pruning back extensive and expensive techstack sprawl – is the industry’s current greatest hurdle.
The Purpose of Web Security
The global connectivity offered by the web is both a blessing and a curse. On one hand, it’s a major force behind retail, marketing, and networking. For instance, one estimate claims that by 2040, 95% of all purchases will be made via eCommerce. The web can now fit in our pockets, on our wrists, and in between each mechanism of a production line. Any brand can show itself off in new and exciting ways, drawing you closer to interested parties than ever before.
On the other hand, that proximity paves the way for web security threats. On May 7th, 2021, Colonial Pipeline had to suspend all pipeline operations for 5 days. A key infrastructural player, it supplies 45% of all fuel to the East Coast. Russian-backed attackers had compromised its network security via account takeover, utilizing a single VPN account before exfiltrating data and unleashing ransomware throughout. The $4.4 million paid in ransom indicates just how much web security threats have evolved into a major black-market business, and how web security solutions have their
work cut out. It’s estimated that, by 2025, global cybercrime will reach an annual cost of $10.5 trillion. This represents a greater profit than the entire globe’s illegal drug market.
Threats Against Web Security
The attack surface of today’s web landscape offers a medley of different approaches to an opportunistic cybercriminal. The six key threats range from targeting user accounts themselves, to exploiting core principles of site loading mechanisms.
#1. SQL Injection
Structured Query Language (SQL) is used to request and retrieve data from a database. SQL injection takes advantage of when a site asks for user input. Instead of inputting login credentials, however, an attacker will include an executable string, lending them access to the core database. This can escalate to full administrative access of an internal device, or even large scale theft of personal data.
#2. Cross-site Scripting
Often used in conjunction with phishing attacks (see below), cross-site scripting sees an attacker attach malicious code onto the end of a trusted URL. A browser assumes the site’s legitimacy, and so executes the attached script. The attacker can access any cookies, session tokens, or other sensitive information retained by the browser, essentially handing over login and device information.
#3. Password Breach
Exemplified by the Colonial Pipeline case, a reused, leaky or compromised password can spell disaster for underdeveloped data loss prevention (DLP) strategies. It’s one of the most common causes of web security attacks, with verified login credentials making up a significant chunk of the illicit cybercriminal market.
Code Injection is a more general term for any attack that relies on an application executing untrusted data. These web security attacks are largely facilitated by poor data handling and insufficient sanitization of inputted data.
#4. Code Injection
Code Injection is a more general term for any attack that relies on an application executing untrusted data. These web security attacks are largely facilitated by poor data handling and insufficient sanitization of inputted data.
#5. Phishing schemes
The human brain is unpatchable. Phishing takes advantage of this via social engineering and spoofing: for instance, a subtly misspelled URL can dupe even security-conscious employees into typing their credentials into a fake Office365 login screen – particularly if the illicit email presents a threat that your account is already hijacked.
#6. Malicious redirects
Web browsers are particularly fallable to redirection attacks. Though redirects do have a legitimate use – for example in secure payment screens – attackers can hijack the browsing process by including a sneaky redirect in an otherwise-legitimate-seeming URL. This can send you straight to an attacker-controlled site, opening up the doors for drive-by downloads and malvertising.
How Does Web Security Work?
Web security is often maintained through a stack of solutions, with each organization prioritizing their own approach. Guiding every decision are three core goals: to monitor and assess web traffic for compliance; protect internal networks from illicit actors; and keep personal data within secure databases.
A full stack aims to deliver a comprehensive approach, with each component playing an individual role. Following the path of data from end-user to website, here are a few of the key web security solutions:
Browser Security Extensions
Offering protection that preserves the user experience, browser extensions provide a browser-native form of defense. While traditional extensions such as ad blockers can sit at the end-user’s device and prevent malvertising campaigns, they still present a risk.
Mass-market third-party extensions often hold permissions to read and change data on any website visited, opening the door for attack. Organizations need a purpose-built browser security extension that actively scans every component of an untrusted webpage. By moving the analysis of malicious code and files closer to the end-user’s local platform, latency is removed.
Next-gen browser security extensions also offer adaptive policies, facilitating a cohesive threat response that spans an entire organization. Finally, the user account can be protected by closely monitoring the browser’s own activities – helping to identify and prevent data exfiltration attempts. Browser security extensions have evolved significantly since the first ad blocker; many organizations are yet to take advantage of this.
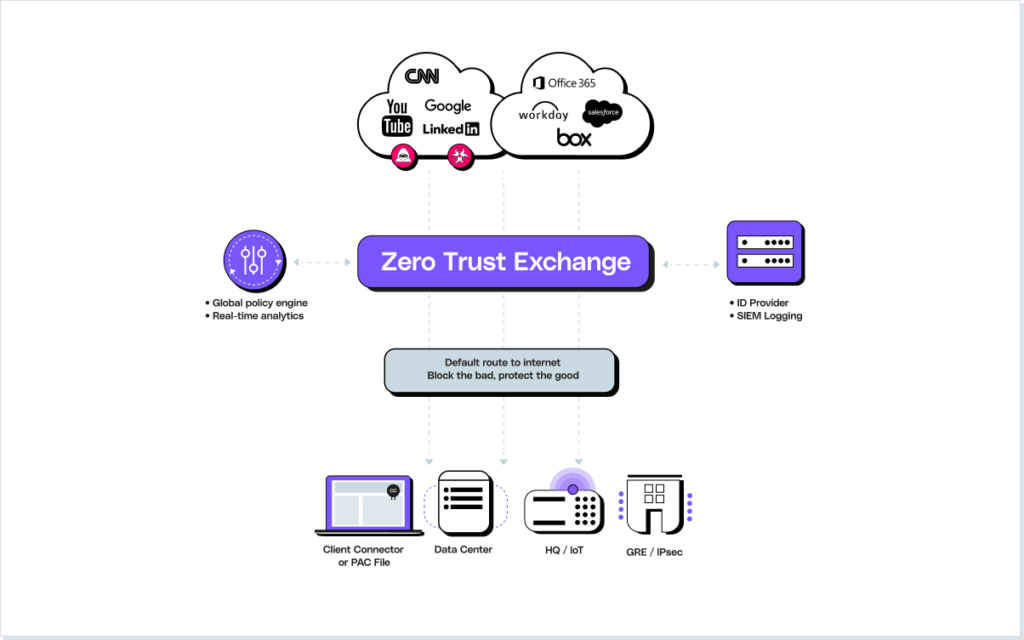
Secure web gateway (SWG)
Starting at the end-user, this solution acts as a proxy between the device and an untrusted site. Instead of connecting directly to a website, a user accesses the organization’s SWG, which is then responsible for connecting the user. As it does so, the SWG inspects the connection for any malicious content by comparing it to a pre-built list of known malicious sites. It also allows an organization to uphold their web use policies by blocking access to inappropriate content.
One of the major challenges presented by a SWG tool is that set up is typically in the form of a stand-alone environment. This makes integration with other pieces of organizational security infrastructure remarkably difficult. Lacking coordinated workflows, logging, or reporting, it can often be a thorn in the side of cohesive protection.
Browser isolation
Whereas SWG acts as a proxy, browser isolation aims to physically distance the end-user from the untrusted server supplying the website or application code. Remote browser isolation is one of the most widely-used iterations; this conducts all web browsing on a server controlled by a third-party cloud vendor. With the site script being executed on this server, a graphical representation of the website is beamed back to the user. Any mouse clicks and data entry is transmitted back to the cloud server to perform, allowing for the end-user’s device to be kept isolated.
While this can help establish a cloud-native approach to security, it’s worth noting that the user experience is often significantly impacted. This has led to instances of patchy organizational protection as users prioritize lower protection over an unreliable and frustrating browsing experience.
TLS/SSL decryption
As the user’s (indirect) requests reach the outside server, the server begins to send data back. From a security standpoint, we still don’t know what these packets contain. Encryption has long played a vital role in web security, preventing spying eyes from accessing in-transit data. It’s why most data today is transferred over Transport Layer Security (TLS)-encrypted connections. While sensitive data benefits immensely from uncrackable encryption, it goes both ways: encryption also hides malicious data packets.
TLS and SSL decryption describes how encrypted traffic is unscrambled; it forms a critical foundation that supports the next piece of the web security tech stack. While crucial for many of these tools, decryption is highly computationally intensive, making it yet another component to add to overall network latency.
Firewall/IPS
With the end-points secured and traffic decrypted, the firewall is the first line of defense against malicious data packets. The precise filtering occurs based on the policies laid out by a security team, helping the firewall remove any packets recognized as suspicious.
An intrusion prevention system (IPS) sits inline immediately behind the firewall. This solution is very effective at detecting and terminating any attempt at exploiting unpatched web app vulnerabilities. When a widespread vulnerability is discovered, a critical time period follows where threat actors can make use of the exploit before the release of a patch. With signature detection, an IPS can block malicious traffic, while also configuring the firewall to help prevent future attacks.
Sandboxing
While the above measures help protect a user in real-time, sandboxing is one solution that pertains to long-term risk management. Similar to a virtual machine, it allows for the isolation of malicious scripts within a secure container. This is incredibly useful for up-to-date attack intel, as live malware can be caught and analyzed without risking contamination of internal networks or devices.
Antivirus
As web connectivity acts as the primary vector for many forms of malware, an antivirus solution can help seek out infected files, and prevent further scripts from executing on an unprotected device. Ransomware, spyware and trojans can all take advantage of only a single oversight, meaning that an antivirus can sometimes act as the very last form of defense. Antivirus programs inspect all traffic flowing throughout the tech stack in order to identify any recognisable instances of malware.
The Benefits of Web Security
The key benefits of enterprise web security lie perfectly in parallel to long-term success. For instance, regulatory compliance is a key factor to commercial partnerships and consumer good faith. After all, the trust imbued in an organization to store data responsibly is quickly broken in the event of a breach. An increasing number of regulations today, such as GDPR and CCPA, are focusing on the protective measures your organization places around sensitive information. Top-notch web security should provide full visibility and control over the databases in your company’s care, and give you full insight into who’s accessing what.
With remote and hybrid work becoming mainstream over the last few years, DevSecOps were suddenly faced with the sisyphean task of maintaining organizational security with web security solutions that were simply not built with cloud transformation in mind. Modern web security solutions allow for employees to work from the comfort of their home, while their device is still subject to and protected by enterprise security policy.
Finally, web security protects employees and mission-critical operations against malicious downloads. Just as Colonial Pipelines had to shut down for several days, instances of ransomware and spyware can completely disable operations, while leaking confidential IPs and blueprints to competitors and hostile governments. The ounce of prevention provided by modern web security is better than a $4.4 million ransom ‘cure’.
Protect Your Browsing with LayerX
The sheer complexity of today’s web security tech stacks is out of control. Cybersecurity professionals face severe burnout. Cybercriminals continue to plunder sensitive databases with little regard for pre-existing security solutions.
This is because today’s security stacks are largely unfit for purpose. Most components were built far before the web browser became a leading operational tool within daily operations; adding fuel to the fire has been the demise of the organizational perimeter, which has seen the transition of databases and other key resources into segmented third-party solutions.
LayerX offers a single browser security platform, based on an Enterprise browser extension. LayerX’s web security service implements at the user identity level, offering its full suite of protective
capabilities from anywhere a user accesses the web.
Accessibility doesn’t define just the user experience. LayerX builds a high-resolution risk profile as the user browses thanks to its in-depth focus on every browsing event. At the heart of this process lies the Plexus Engine. It continuously monitors browser changes, page behaviors, and the user’s own activities. All of these events are clustered together, enriched by the supporting LayerX Threat intel cloud, and analyzed to assess its risk context in real time.
With near-zero impact on the end-user experience, the LayerX browser extension is able to pinpoint malicious activity within any component hiding in an accessed web page, before preventing browser interaction. LayerX is purpose-built to give security teams the right tools to protect customers and employees in a cloud-first landscape.